

Blogs 
October 3, 2022
Living Security Team
The Big Disruption in Cybersecurity: Webinar Takeaways & Recording
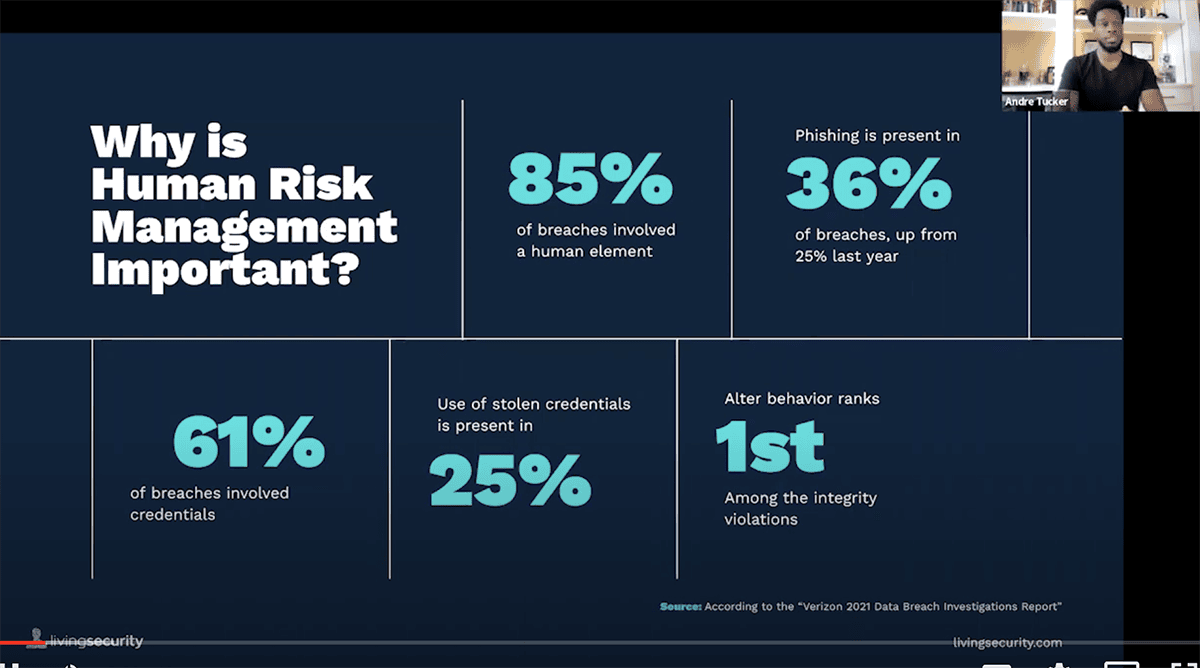
Today cybersecurity awareness has moved beyond “checking the box” of completing training. The “Verizon 2021 Data Breach Investigations Report” shared that 85% of breaches involved a human element; it’s time to truly impact behavior. We’ve evolved from security training to human risk management, and this webinar highlights some of the exciting ways that empowering teams with knowledge creates a culture of responsibility and fun around keeping cyber threats at bay.
Living Security’s own Jenny Kinney, Senior Strategic Client Advisor, and Andre Tucker, Principal Product Strategist, share key points in this webinar from their work with Fortune 500 companies.
Here is a high-level comparison of the difference between Security Awareness & Training and Human Risk Management approaches.
Security Awareness & Training focuses primarily on:
- Compliance. Making sure everyone completes (and passes) the annual (boring) training.
- Org-wide training. One-size-fits-all training that is not meaningful or relatable (and doesn’t “stick”).
- Phishing-centric. Focusing on tactics instead of human behavioral change.
- Light on data. Check-the-box: Did everyone complete the training?
Human Risk Management focuses on:
- Data-driven approach. See vulnerabilities throughout the organization and tailor training where you need it most.
- Behavior-based training. Focus on the human behaviors that keep your organization at risk.
- Role-based training. Privileged users need different tools; financial teams may be more at risk. HRM ensures the right people get the right information at the right time.
- Culture change. When you change behaviors, you change the way you work together. By making risk mitigation a company-wide priority, people learn together, take responsibility, and make it fun.
- Behavior change analysis = ROI. Real behavior changes can be measured across the organization, and these changes help security teams protect revenue, business disruption, and employees themselves.
Learn more by watching the webinar recording and/or reading the transcript below.
Read the full transcript of the webinar here.
Jenny Kinney:
My name is Jennifer Kinney. I am one of the client advisors here at Living Security. I am actually a former Living Security client myself. I joined the team here about a year and a half ago, and I'm happy to be part of this innovative team. It's a ton of fun working for a startup. I've been in information security for, this is my sixth year or so, and I really have just a real love for the industry, changing human behavior, et cetera. I'm excited about our conversation today. Andre.
Andre Tucker:
My name is Andre Tucker. I am the Principal Product Strategist at Living Security, working a lot with our unified platform and our other products on security content. My background is in data and cyber security. Prior to this I was global cloud architect at Splunk, and then prior to that was in the MSSP space for the better part of a decade, working with advising CSOs on program strategy. It is very nice to be here with you all, and especially with my co-speaker, Jenny.
Jenny Kinney:
Thank you. They put us together. Andre's more technical. I was a psychology major, so I'm all about the human behavior side. So together we kind of make a good team when it comes to information security and human risk management.
Andre Tucker:
I would agree. Awesome. Our agenda for today, the biggest thing that we're going to cover is the difference between human risk management and traditional security awareness and training. Then we're going to go into a deep dive around measurements, insights, and data and how to effectively use those, talk about actions and implementation guidance, and then talk about the necessary program adjustments that you'd need to make in order to make this very successful at your organization. Why is it important? I feel like if you're here then you already agree with and know these stats, but the human element is one of the most targeted portions of cybersecurity.
According to Verizon data breach reports, 85% involved a human element. And so these are statistics that we see day in and day out, but it really stresses the importance of focusing on humans as a portion of the security stack, the way that we focus on technology. And so going into it, human risk management versus security awareness and training. I'll let Jenny take this one to kind of discuss those differences.
Jenny Kinney:
Sure, I'd love to. I thought it was really interesting, the poll results, it looked like about 58% of you on the call have heard the term human risk management in the past year. A small portion are just learning about it today. And then roughly 30% have known about it for more than a year or so. It is a newer industry term and we're going to talk about how it is not just semantics and I want to talk about the difference, because when I first heard human risk management, the term, I was like, okay, they're just taking security awareness and making it sound cooler. It's just the latest buzzword. But there actually is more to it than that. So you can take this information with you into your organization as well.
This is a comparison of the two different programs. When we talk about security awareness and training, typically we are talking about just being compliance oriented, trying to pass your audits. We're talking about blanket organizational wide training. So once a year, everybody in your organization gets the exact same training, have to finish it within 30 days or what have you. But there are no different role-based trainings. Everybody gets the same thing. Security awareness and training programs are typically very phishing centric. It can be difficult to have any other metrics to analyze besides phishing clicks, phishing reports, et cetera. And fairly light on data. When I was a program manager in my last role, we would try to prove the return on investment. Like yes, we are actually changing our behaviors. This department is important.
However, there wasn't a ton to go on. We could report on improvements in our phishing simulations, but there wasn't a lot of other things like engagement with our activities, that kind of thing. Other than that we were just fairly light on data. Let's move forward and let's mature our programs into this HRM model, which is a more data driven approach. We're going to have more analytics so that we understand what kinds of behaviors folks are administering or having throughout your organization, and we can target them and improve those behaviors. We can do role based training. This is extremely important. We want your employees to know the why at each role. For instance, a salesperson is going to have a different, why do I want my organization to be secure, differently than an HR person or somebody in finance.
So sometimes salespeople can be hard to convince that cybersecurity training is important. However, it would be very difficult to sell a product when you are on every news channel because you just had a breach. Let's talk about the why and the how at every role. We are trying to encourage an entire culture change in organizations with HRM. That means that everybody in the organization knows that it's important. Everybody in the organization understands that security is the job of every single person. It's like steering a big ship around in another direction. We're going to talk about ways you can actually change culture in this presentation.
And then like we are saying, we want you to be able to prove the return on investment in your program. And so with the human risk management, with the platforms that we have and the data that you can have, you can actually track behavior change much more tactically and accurately than you could with just a security awareness and training program. I want to know, does this make sense to you guys? Give me a comment, let me know what you think about that while we move on to the next slide.
Andre Tucker:
One thing I'd like to bring up here is the behavior based training and the role based training, right? Role based training has been obviously gaining a lot more popularity, which really adds context to that individual. But I think the layering behavior based training with role based training accomplishes two things. It makes sure that those users get exactly the training that they need topically, and we prevent something like training fatigue where because we're blanket assigning training, the training that this individual may need, it may be the eighth training that they get and by that point they've zoned out.
Whereas with behavior based training, you're making sure they're getting training based on the fact that they exhibit a deficiency in that area. The things that they need are what they're getting exactly. And then the role based training, just makes sure that that is relevant to their lives, their context and they can really understand how that particular threat affects them. I think there's a lot of power in layering the two of those concepts at the same time and using data to drive that approach.
Jenny Kinney:
Eric wants more details on that, so let's give him some.
Andre Tucker:
Absolutely. Let's do it. We're going to talk about measurements, insight, and data. This is kind of the core of that data driven approach. We're going to talk about which measurements and insights can and should be captured and what technologies provide that valuable behavior data. All right? And so you're going to see that it's not just semantics, right? There is a need for this shift and we're going to show you how to make it happen with these measurements in data. One thing that I like to talk about before we get into this, is really the emphasis on the need. I love this quote by Jinan Budge. She says, "The key disruption in security awareness training is that we're not training people for the sake of training them anymore. We're training them to really drive behavior and culture change and move towards fostering real performance action."
We're not going to be looking at whether or not people pass or failed quizzes as a part of these metrics. What we're really about to be looking at metrics for is based on their actual behavior, what are they doing in the environment and does that align with the practices that we show them in our content and we test them on in these assessments? First, let's cover measurements, insights, activities. What does this all mean? We've got data sources. And those data sources could be Office 365, Okta, really all of your technologies that you use from a business and security standpoint at your organization. Now, those will give off individual events and we can call each one of those individual events and activity, right? User A did thing one.
Those types of activities are good for measurements. This is where security awareness training programs have been in the past measuring things like phish clicks, user click phish, here's the number of phishes that they click. I think it's good to understand how often users are doing activities, but it doesn't really provide you insight into their behaviors. What we do is we start to introduce different correlations between these activities and these device types to really create insights so that we can understand what is it that this user may or may not understand about security, and where do we need to focus more?
One great example is looking at the Okta data set where we can look at password resets and we can look at compromised credentials. But once they are correlated, we can understand that this user has reset a compromised credential. And at that point we are identifying a vigilant activity that this user has taken. And so that is another big thing that I like to call out with human risk management, is we are not just looking at risk, we are very much looking at vigilant activities as well. Who in the organization is doing things to actively help defend the organization and is showing that they're putting security at the forefront of everything that they do?
Jenny Kinney:
We like to reward these people and let their managers know that they're exhibiting positive behavior.
Andre Tucker:
Absolutely. And let the organization know really, right? Because we want to get other users to emulate these behaviors. And so when we look at these things, we can make sure that we're identifying those vigilant activities, but also the risky one. The example below where we're looking at Cisco Umbrella, Netskope and Proofpoint, this is where we can start to identify things like, yes, our user click to phish and we can understand that, but not all phish clicks have the same risk associated with them. If I've got a user who clicked a phish but also was allowed to the website and passed credentials or submitted some type of information to that website, well at that point we understand that this user maybe logged into an account through a link that they got from an external domain, that turned out to be a phishing email.
That provides us the insight that we need to understand to tell them that they really need to be able to identify phishing emails, but they also need to understand web behavior and understand that instead of clicking the link, perhaps we should navigate to that site on our own and then supply our credentials. That way we know we're not getting misdirected.
Jenny Kinney:
It's happening so much right now too.
Andre Tucker:
Absolutely. And so I want to take you through how we essentially come up with these use cases and these behaviors and what should we be identifying. There's a lot out there in security and each organization is different, each industry and vertical is a little bit different, had different things that impact their business more than say another company. And so the first thing you want to do is really identify, what are those things that we are really sensitive to? And so for some organizations that may be account takeover, right? Of course it applies to everyone. But let's say this is the most important thing to us. We can go ahead and start to break this down into understanding, what are our objectives when it comes to account takeover, right?
We want to reduce the likelihood that that's going to occur. We want to decrease how long compromise credentials are out there and valid. We want to reduce enterprise credential reuse. And perhaps to make it easier to do that, we also want to increase password manager installation and usage. So once we've identified our objectives, the next thing you want to do is really focus on, what are the behaviors that we would need to change to make those objectives a reality? And so some of those for this particular case are usage of weak or common passwords. All of that leads to account takeover. Credential reuse across multiple accounts. We want to change how often users are clicking on links and downloading attachments from unfamiliar sources since that could lead to malware, that leads to account takeover.
And we want to maybe mitigate the impact. We want to install multifactor so that if credentials are compromised, at least they don't gain access to the account without that multifactor piece. So next, we've identified behavior, we've identified the objectives, we want to think, what types of correlations or insights do we want to put together that will highlight these activities, so that we can then measure the risk associated. And so for insights, they may be insights around credential compromise and credential management, right? Things around account log on analysis, MFA enrollment, and even training performance. We want to know are these users understanding the security threat and simply not putting it into practice? Or is there a deficiency there that we really need to fix, maybe by hosting a lunch and learn to bridge the knowledge gap.
And then integrations, right? Because this is where the rubber meets the road, is what do we need to integrate or collect data from in order to get visibility over these activities? And so the way I like to think about that is, what technologies hold events that would show me these types of information? And so we will have something like single sign on, multifactor authentication logs, password managers, and then even breached data, so that we can understand when accounts have been compromised and then start to look at what behaviors are taken after that.
And so at Living Security, we do have our unified platform that we use to conduct human risk management and quantification. And this is the thought process that we go through when we create our focal points. And that's essentially what this is. Now, there are many different focal points, but that was simply one of them. Now, let's see. The next one is phishing management. This is something that is in context. It's the same process that we took with account take over prevention just around phishing. Now one thing that you'll notice here is that it does go far beyond just looking at click rate and understanding click rate. We're also bringing in email security logs and LMS and training so that we can understand email behavior.
How often are users quarantining or releasing emails from quarantine, phishing proficiency from a simulation standpoint as well as a training module's perspective. And how susceptible are our users to falling for a phish and how often are they targeted? All of these things are brought together to understand a much larger context of phishing than simply, did they click a link and did they maybe supply their credentials to a phishing campaign? Perfect.
Jenny Kinney:
Andre, go back just a second and hang on that slide for a couple more seconds so people can take a screen grab if they want to, because there's a lot of good information in there. I just like how we're talking, we're not saying that phishing simulation metrics aren't important anymore, but there's so much we can do with it, so much more we can do.
Andre Tucker:
Absolutely. And really it's all about understanding their behavior and context in full context of phishing, not simply one activity that leads to phishing, right? And so I think that's really important. Now, when it comes to the insights, here's some samples and examples of insights. But one thing that I like to focus on is the area in the pink boxes. Traditional security awareness and training has focused solely on these three areas of identifying phishing, looking at training completion, and then pass and fail rates for end users. And while that's great, there's a lot of additional area in the security world where an organization could become compromised and those areas do have human elements that we need to be addressing and making sure that our users are aware of.
And so because of that, it only makes sense that from a human risk management perspective, we monitor those areas and look for insights and measure the risk associated with the human behavior and also identify the good things that users can do to help the organization in those areas. So for our unified platform, we do have six security categories. And so authentication, data security, web security, device phishing, and then training. There are different topics or subcategories within each of these categories. Now, this isn't all inclusive, but this shows you an example of the types of behaviors that you want to be looking for in each one of these categories. One that I like to call out is maybe the credentials portion of authentication and access.
Maybe one of the insights or correlations that you can figure would be looking at compromised credential account activity without a password reset. So someone has been shown as they got compromised credentials, they are active in the account, but the account password has not been reset. Now, one of the actions you may take from that could be to put in place a process and automation that when your credentials are discovered in breach data or there's any indication that they're compromised, automatically trigger a force password reset for the user. Some of these actions to remediate these activities may not be, hey, let's train the user a bit more. It could be something technical or it could be something process based that is a highlight that you need to develop a little bit further.
Jenny Kinney:
I like that automated approach as well. Automatically insisting that people change their password, I think that's great. And you want to make it easy for people to do the right thing quickly.
Andre Tucker:
Absolutely. And so that's one example of an insight followed by some type of action that we would take after that. I think if you want to screen grab this one as well, please do so, because I think this is a lot of good ideas around what you could be monitoring and measuring outside of phishing that would have a lot of impact to your organization security posture.
Jenny Kinney:
And Jake, yes, the presentation will be available following, we'll send everybody a link to it and it'll be transcribed as well. And Eric and Brooke, I know that you were looking at, wanted to know about some more behavior, so I hope this helped.
Andre Tucker:
I think Steve asked a good question in a chat, recent studies by Cyentia were talking about the 5%, how 5% of your users cause like 90% of the risk or something like that. Don't quote me on the numbers, but I do know the study you're talking about. And so he's asking, is there a trend to focus on special needs employees as opposed to the entire population? Honestly, that is the entire premise of human risk management, is really addressing the employees and the behaviors that pose the most risk to the organization and not sending out blanket training. And so what we do with our unified product is we do have insights into all of these categories, and here's an example of some of those insights, but essentially we can split our population into segments.
And this is something that you could do as well, if you try to say, stand up these correlations in a BI tool or use maybe spreadsheets as an initial start to collecting metrics, is start to look at things like your population segments, like your departments, or look at maybe all of the users in a particular region, so that then you can understand and identify different trends that allow you to really focus on the root cause. If we understand that one department seems to have all of the let's say URL clicks from quarantine released emails, let's say all of it comes from one department, what is it about that department that's different from everyone else? Are they not receiving a specific training that everyone else is?
And it lets you really focus on the root cause of the behavior as opposed to just the behavior itself and assigning training. That's one example of how you can make different targets or you could just target all users exhibiting a specific behavior. That is something that we see a lot of organizations doing once they use unifiers focusing on the 5% and also focusing on those top behaviors that introduce risk.
Jenny Kinney:
Andre, do you want to talk about the crawl, walk, run? Because if you have a less mature program, we don't expect you being able to use all of these insights at once, but you can start taking a more strategic approach with let's say a couple of them.
Andre Tucker:
Exactly. That's where really, and I'm going to actually back pedal a little bit, but that's where the targeting in your use cases really comes into play. This is what's going to allow you to crawl, walk, run. There may be a lot of technologies that you have at your disposal, but once you go through the practice of identifying what your major use cases and what your objectives and behaviors you want to change are, you can be very prescriptive about choosing which integrations you start to collect data from and which insights you start to create correlations for or get visibility over. And so you'll notice that this focal point is what we call them in unify. So these are already all pre-built with our unified platform.
But if you do this on your own, you'll notice that this use case might only require three integrations, which is a great way to have a small chunk of integrations to start with and provide a lot of visibility and impact. After that you would just simply build on top of that and add two to three maybe more additional integrations focusing on another topic until you've covered the full gambit of what risks are posed to your organization. Okay. All right. And then data sources. This is very much just a highlight of our categories. Identifying some of the technologies that you may have in your organization, that would provide a lot of rich behavioral context for that particular category.
So web, we're focusing a lot on proxies, SASE and CASB solutions for data. That's obviously going to be DLP or data discovery, data classification. I would say take a screenshot of this because chances are that your organization has a lot of these different technologies. And so when you start to think through your use case and you think about that integrations portion, this would be a good reference to say, all right, if I'm going to focus on phishing, I know that encompasses email, I may need one or more of these technologies in the email category to get that visibility.
Jenny Kinney:
I'm just answering Eric in the chat right now. Okay. We want to talk about once you have this information, how you can use it and disseminate it throughout your organization. So if you look on the left, we have this user report card example. This is at the individual level, so we can see Jane here is exhibiting behaviors that put her at a high risk for the integrations that we have available. And then you can dig in and see exactly what are those behaviors. Eric, that's a popular sentiment you have there. We can have leader boards, which I think is a brilliant thing to do because the heads of these departments didn't get to be the head of a department without being competitive.
So if I were, let's say the lead of the help desk for instance, and I saw that I was falling short, my team was having the most risky behavior, which would be very dangerous for help desks to have risky behavior, I would start to be competitive and want to increase my numbers, talk to my people about their behaviors, make sure they're getting the training they need, paying attention to it and understanding the importance of their security behaviors. And on the right here, again, we have these department snapshots where you can slice and dice your information by department, you can slice and dice it by geographical location, whatever your interested in, which I think is really important.
When our clients they are sometimes going on road shows now or targeting different offices. Before you go, you can actually take a look and see, okay, in this office phishing is no problem, that's great. However, there's a lot of risky web behavior, what's that about? So that you can really take this information and give it to the people that need it. Don't waste your time on phishing if everybody's reporting and there's been very little phishing clicks or activities there. We just have a couple examples. These are what you would get in the platform, just slice and dice it. It's really beautiful too. It's just great. You click and then you can drill down and see the exact behaviors as much as you want.
You could probably go down a rabbit hole with this stuff. I would probably just analyze it all day long. But anyway, that's what we have there.
Andre Tucker:
I like to talk about the user report cards versus the departmental snapshots. I think it's two different approaches to get to the same outcome of users changing behavior. On the one hand you've got the user report cards where users can govern themselves. They can be responsible, understand what it is they're doing that poses risk to the organization, but also what things that they're doing great that, hey, maybe you need to do more of or get others to do more of. That's one perspective. Now, me personally, I got report cards in high school all throughout school, and if you gave me my report card, I just know me as an individual, I was not going to give that to my parent and I definitely was just going to act like I never saw it. It didn't happen.
Jenny Kinney:
Andre.
Andre Tucker:
I'm sorry. But for those types of individuals like me, that's where the departmental snapshots come into play, where you're fostering a conversation with that department head so that they can work on addressing the behavior of the individuals in their section of the business. Our co-founder, Drew, he's a veteran, I was a veteran and he uses an example that I actually love, which is you more likely to follow your sergeant than you are your general, the generals all the way up at the top, but you don't really know that person. You don't have a relationship with that person. Same thing for security, right? Security says something to a user, I get it, sure. But if your direct supervisor says something, you're a lot more likely to take that feedback to heart, listen and kind of develop it. That's where that can play. It's really two different angles of addressing the same problem and both of them can be implemented at the same time
Jenny Kinney:
And effective. Okay. Now we're going to talk a little bit about the psychology, really taking this information and implementing it into your programs. I like to encourage everybody to make your communications interesting, varied and relevant. We are all kind of tapped out when it comes to seeing new information, so please make it interesting and relevant and don't make it dry. We are a bit of a, you can see we like the gifts. You can probably go ahead and stop this one. I know it can get a little annoying. But we like gifts, we like memes at Living Security, but other people, other cultures may like something a little less in your face. So entertain as your culture allows.
But I do want to encourage you to make your communications interesting and relevant to the audience. As much as you can tailor to your audience, please do, makes it better. And then also like I am a Slack person. Emails stress me out for whatever reason. I'm not going to read a newsletter, I'm just not. But I would look at a Slack channel. I'm just like, that's my favorite way to communicate. Other people in your organization may love a newsletter and just set them aside, read them during lunch or whatever. Take advantage of all these different communication channels so that you can meet people where they are and make friends with your communications department please, buy them lunch, give them swag, whatever you need to do to better them up so that they will take your communication seriously. I promise it helps.
I wanted to talk about policy changes. If these are part of, even if it's a technology policy change or if it's a change to your actual maybe computer network security policy, make sure that they are communicated, they're easy to obtain and they're easy to understand. Sometimes these are so technical, your end user won't understand what you're talking about. So look at things with that lens. You may be a technical expert, but not everybody is. So make it easy for people to understand and to do the right thing. And again, use lunch and learns. You can have targeted lunch and learns, role-based lunch and learns. We like to do quizzes here at Living Security. Just that competitive edge really gets those synapses firing, makes things fun and easy to remember.
We have virtual escape rooms at Living Security that are a lot of fun. They're team building and it's an immersive experience, where you can really dig in, reinforce your most important security concepts while you're having a good time. Again, that improves retention. And it's difficult these days for teams to a really bond and get together in our hybrid and virtual world. So that's a fun thing that you can do. We have a lot of clients using that during security awareness month, et cetera. Like we've been talking about, answer the why at all of your roles and levels, so that people understand why it's important to them. Be empathetic with your different audiences. Everybody's busy. People are having to do more things with less.
So understand that and say, changing habits is difficult, but it's important to say slow down before you click on a phishing email because one click could put our entire organization at risk. It's pretty unbelievable. Again, use role based and behavior based training. I love to encourage people, and most of our clients are doing this, incorporate at home advice for families. I almost feel like if you start really helping people, give them the tools to educate their children, educate their more vulnerable loved ones, et cetera. I can't say your grandparents, but sometimes they're really highly targeted. So think about these people, what they're seeing. It can be a value add as an employer if you are giving people this education, because security threats are everywhere.
Neurologically retention will improve when these, your communications are varied and relevant to them. That's all we really care about, is changing behavior and it is difficult to change behavior. So you have my sympathy and my empathy being tasked with this. And Leigh, would you drop that link that I showed you earlier. As I was preparing for this presentation with Andre, I was reminded of a study that was done in the UK that my buddy Robin, he's a CISO at Relics told us about a few years ago. I would love for you to take a look at it. It's really interesting talking about messaging. If you are comparing, let's say you have 2% of people in a department who are still clicking on phishing simulations.
If you tell them in your department, 98% of people are reporting a phish or are vigilant against phishing, however, you are still not noticing that. It's like, oh my gosh, I'm falling short in my department. I am on the naughty list. The study is cooler than I'm telling you now, so take a look at it and you can see the different kinds of messaging that had the most effect when it comes to behavior change. This study was about getting UK residents, and I think we have a few on the line to pay their taxes. So you may have heard of it. It was a big behavioral study, it was very cool. Okay, talking about encouraging culture change. Again, it's like steering the ship in the other direction. It can be really difficult. Take a slow and steady approach. This is very serious, but it's also nice to have a little bit of fun.
At a former role I did something called phishy Fridays where throughout our big campus, our larger campuses, we would put out Swedish phish with signs about fighting the phish and that type thing. It would really spark conversation just anecdotally. That's something that you can think about and I know a lot of you out there are already doing a lot of fun things. Let's see. Thanks for dropping that, Leigh. I appreciate it. And then security champions programs. We encourage folks to designate people, perhaps your most vigilant performers that you have extrapolated from the data, those that are really interested in cybersecurity throughout the business. You can designate them to help you out with lunch and learn and spreading the word about behavior change. Perhaps if a policy has changed in their department, they can help you with that.
And I actually have a one pager in our community. I'll tell you how to join our community. If you don't already have a security champions program, then I have a one pager to just give you some tips and tricks on getting started with that. Okay, the psychology of winning, think about the first time and last time you won something. Let's see. Okay. The first person that answers this question is going to get one of those $100 DoorDash gift cards. Okay? So listen and everybody pay attention to whoever comes in first. Thanks for dropping that about the security champions link, Cassie, good job. Somebody tell me the last time you won something in chat. Okay. Anne Simpson. Okay, you won something yesterday. Tell me what you won.
Andre Tucker:
I love that most people are like me and have never won squat. I empathize with all of those individuals.
Jenny Kinney:
Okay. You won a gift card for training. Amazing. Okay, well that training is going to stick with you. I remember the first time I won something, it was a jar of jelly beans in fifth grade because I was the closest to guess the number of jelly beans, hasn't happened since, but I got lucky that time. But I will remember that day for the rest of my life, obviously it's been a while. Think about the psychology of winning. People love to win stuff and they will listen to you, become more interested in your program if you can give them something. So use lotteries and raffles to encourage vigilant behavior. Let managers know their employees are practicing security.
I want my manager to think I'm smart and I'm doing a good job. So let them know. Pretty much everybody feels that way. And I think Andre mentioned this earlier, public recognition at all hands meetings, newsletters, Slack channels, et cetera is great. Anything you can do to get folks excited about security.
Andre Tucker:
I want to comment on how it's ironic that Anne won a gift card for training and now she's winning a gift card for telling us about her gift card that she won.
Jenny Kinney:
I think it's time to play the lottery. Okay, time to go, Anne. Go do it. For those of you that said never, we'll choose one of you guys to win the other gift card so that you can tell everybody you're now a winner. Okay? There's qualitative and quantitative metrics you can use, that culture is changing and risk is reducing qualitative. More questions are coming in Slack, email and other channels. You may see an increase in incident reporting, which is great, this one's always kind of funny to me because it's like, oh yeah, more people are reporting incidents. I hope that's because they're being more vigilant and not because there are more incidents, but there we are.
Training completion and dwell time. If you have really entertaining training and people are interested in taking it and interested in cybersecurity, you're going to have more people finishing it on time and quickly and there will be less past due notices because people want to take it. We've got some great training here. And then improve security policy alignment, so you're seeing less notifications that people are not adhering to your policies.
Andre Tucker:
Okay. Perfect. And then measuring program results and actions on ROI, right? I'll go through this very quickly. So you definitely want to measure culture, that's how engaged your organization is. But what are the results of that culture change as well? Looking at the image on the left, one thing that our unified platform does, is it really looks at risk of each individual based on multiple factors. And then we can start to understand, after we do different actions, how many users change risk buckets? That's one way to quantify, that is we had X amount of individuals that were somewhat risky yesterday and now we've got this many, right? Very easy metric to understand. But additionally, looking at the trend of activities and insights on the right and understanding how were these activities trending prior to our action and then after our action.
Obviously we want to move the needle for those risky insights and risky activities in the downward trend direction. And if we don't see that happen after our activity, then we know that we may not have moved the mark on them changing behavior. We need to try something else for these individuals. The good thing about this is once we find out what sticks, we can do that action again the next time. We don't have to go through the trial and effort every time of figuring out what our organization likes to see and what really resonates. So two very simple but very powerful ways to understand the program results. And then present these results back to whoever cares to look at them and make sure that you let them know the organization's doing better and congratulate them.
Jenny Kinney:
Exactly. And if lunch and learns are not working, if lunch and learns are expensive and hard to put together, so if people are just eating lunch that aren't changing their behavior, let's do something else. Spend the money elsewhere. We do want you to celebrate your wins as you start to see that you are moving the needle, pat yourself on the back guys. It's difficult to change behavior. So celebrate the small wins and brag about yourself. Okay. We do have time for a few questions. And if you want to keep this going, a lot of you on here I already recognize are part of the Living Security community, it is a very warm, helpful environment for us to collaborate, inspire each other, share ideas. We've got a lot of great conversations going on right now, especially around cyber security awareness month.
There is the link. If you are not yet a member, please join. Join the community today. If you are a nice person and want to help the other industry professionals out there, and we can keep these kind of conversations going. Andre's a part of it. I'm the facilitator. We can keep talking about human risk management. We'd love to have you. I think we have a poll too it that we can push. Just let us know if you're already a member, if you'd like to join, and if you're not interested at that at this time, that's fine too. Andre, is that all?
Andre Tucker:
I think that's it. I think we've gotten through it.
Jenny Kinney:
Oh yeah, we got one. Do you think that your board is interested in security? That is a great question. I just want you guys to answer that. Is this top down? Are you getting questions about security? Okay. And while we're waiting on people to answer that, we see our organization seeing success in moving human risk management to teams outside security such as communications or HR. Absolutely. That kind of goes back to that behavior role based approach. Communications will have its own particular vulnerabilities. HR definitely does. They have a lot of employee data in their systems. Andre, do you have anything else to say about that?
Andre Tucker:
Yeah. We've seen, at least with our unified product, a lot of teams outside of security starting to leverage it. And I'll just give one quick example of looking at phishing reporting accuracy. Right? It's great if we get the entire organization reporting phishes, but I don't think the SOC thinks so, right? Because they have to review one of those phishing emails. So if we get the entire organization reporting and only 15% of them are actually phish, then we're creating maybe a little bit of disdain over there. So a lot of the SOC teams like to collaborate with the awareness team, and we can get the metrics back from the SIM or back from the ITSM tool in terms of understanding what is the result of this investigation. And when a user reports something and it turns out to be a phish, we can keep track of that.
If users are reporting phishes that are inaccurate more times than we would like, we can then give them very specific training on identifying phish or maybe just have a lunch and learn where we talk to them face to face about what is it they're missing and get that rate down. It really helps that team, that team appreciates you for it, the organization's more secure. And then there's a bunch of other use cases like patch management or secure coding that other parts of the organization like to collaborate with the human risk management teams on. So definitely see that as a trend.