.jpg)
.jpg)
Solutions 
Solutions
Identity Threats and
Account Compromise
A form of identity theft and fraud, where a malicious third party successfully gains access to a user's account credentials.

The Living Security Unify HRM Platform gives you visibility into the most susceptible users for account compromise based on behavior and context so you can take proactive steps to mitigate risk.
Key insights include:
- Suspicious IP
- Suspicious or Impossible Location
- Multiple Login Failures
- MFA Adoption
- Password Manager Adoption
 Identify
Identify
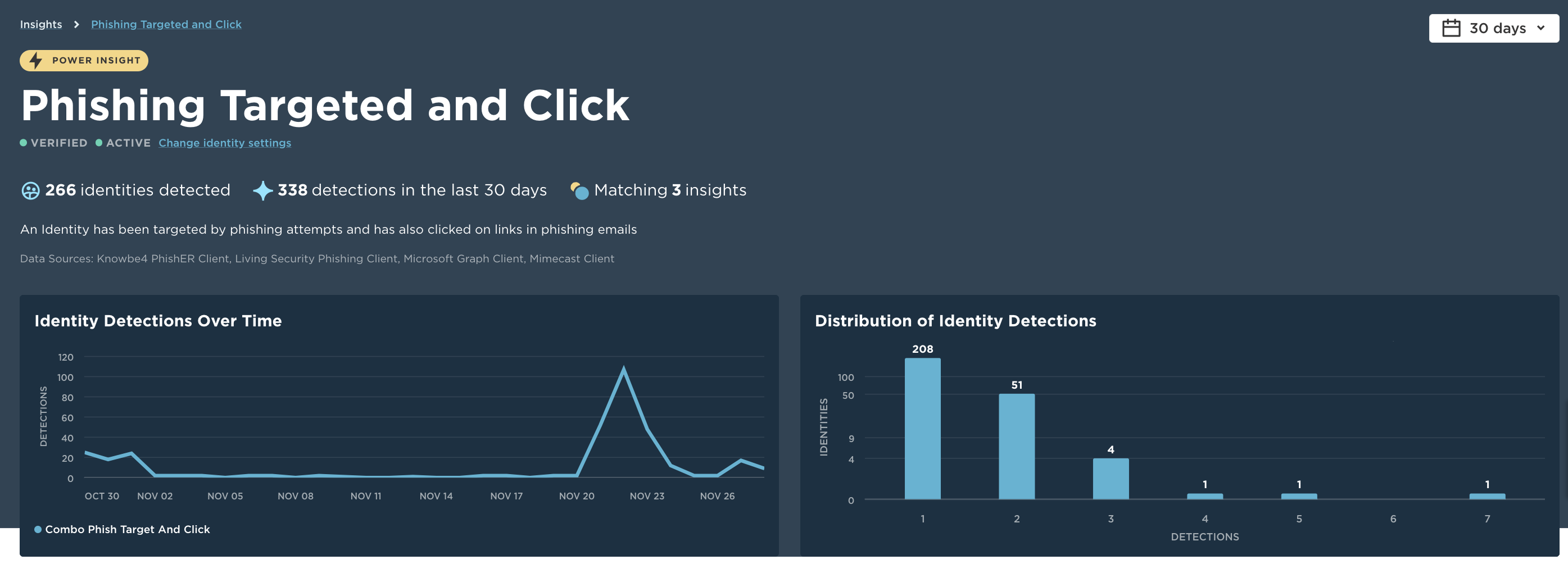
For the first time, analyze related identity threat and account compromise data from multiple tools in a single view. Pull together the group of users that are most susceptible to identity threats based on both the threats that target them and the behaviors they have demonstrated.
In a single pane of glass, Unify helps you identify susceptibility to phishing and identity threats, so that you can take action before the incident occurs.
.png) Protect
Protect
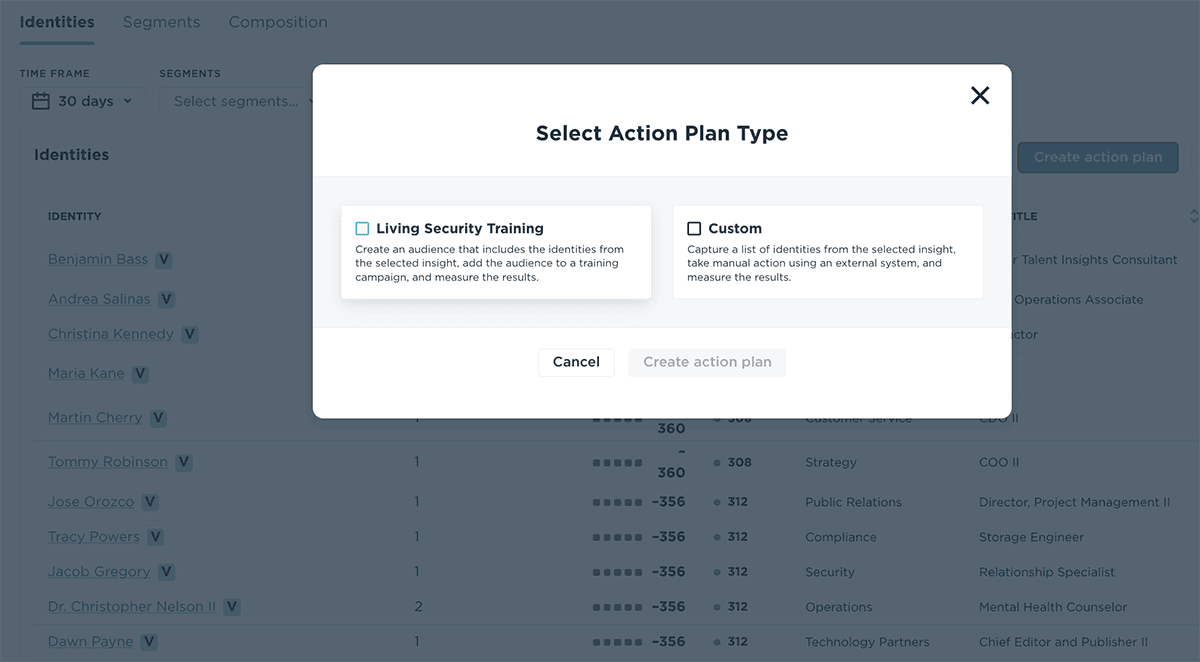
Initiate action plans that include nudges, training, and policy interventions to build up vigilance around your most vulnerable users. Send notifications, update access levels, or assign targeted training to your users with elevated access to key company data.
 Report
Report
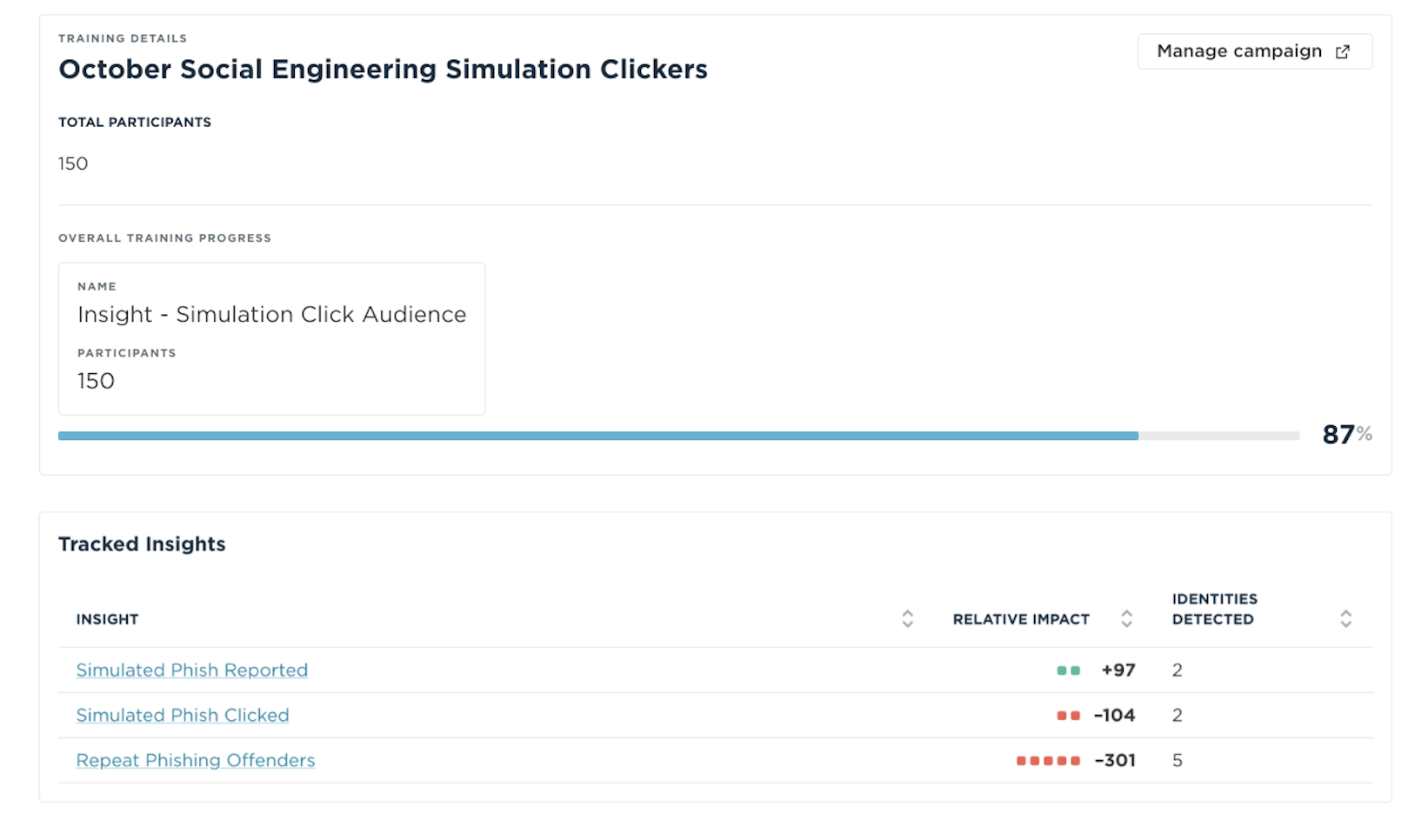
Demonstrate ROI of the mitigation actions with tailored reports that ensure the interventions are creating the desired effect. Beyond tracking training completion or policy acceptance, view the trends in the behaviors you want to address. Observe your highly targeted users, and ensure that risky behaviors decrease as phishing reporting and vigilance improves.
Promote a positive culture of security vigilance. Use scorecards and reports for employees, managers, and executives to foster a security-conscious culture and boost employee vigilance.







