AI-Recommendation Engine pinpoints and automates training and policy orchestration
Protect from security threats with targeted action plans. Save time with an AI recommendation engine based on proven best practices that provide next steps and communication templates to nudge employees to self-address behavior.
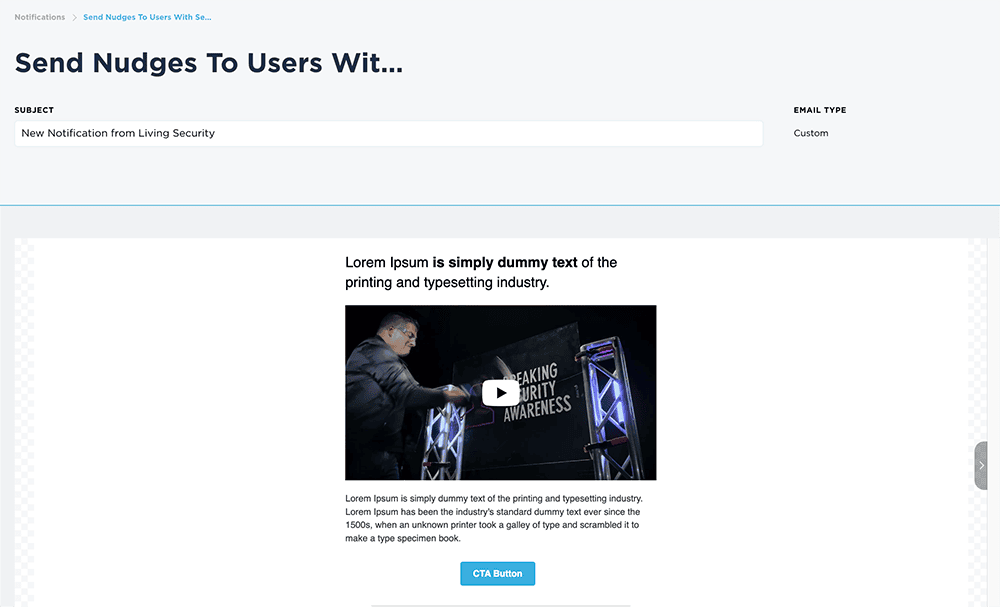
Nudges
Influence and change security behaviors across your workforce with automated nudges in the form of security notifications, messages, and prompts delivered via email, Slack, and Microsoft Teams.
The Unify HRM platform enables automated, intelligent nudges across the full array of security risks, from reminders to update software, change passwords, implement MFA, complete security awareness training and more.
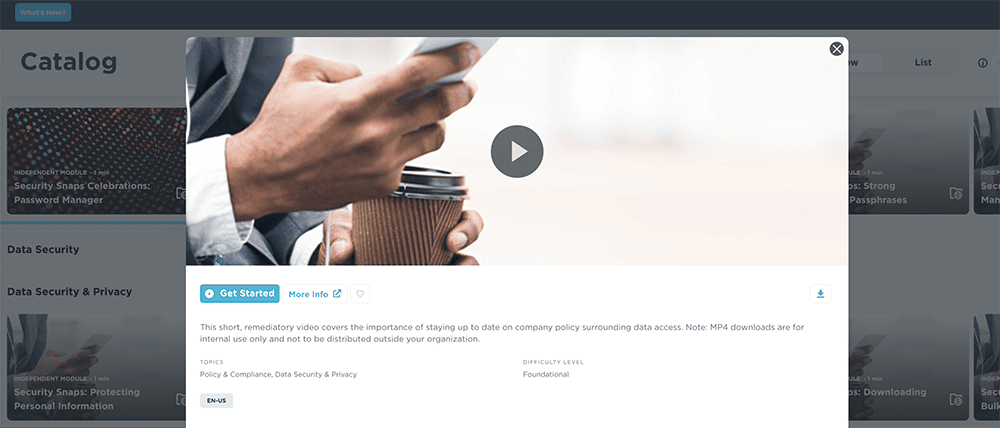
Training
Build cyber-aware champions with personalized, engaging training content that empowers employees to identify and thwart threats early and often.
Meet employees where they are with bite size training that is compelling and can be immersive, and gamified to help drive vigilance that is fun. Engaging and educational content with gamification keeps employees engaged and can accommodate their needs.
Phishing Simulations
Raise users’ awareness of phishing threats through the creation of highly-relevant, personalized simulations spanning phishing (email), vishing (phone/voice), and smishing (SMS) attacks.
Next utilize our Email Threat Simulator and Incident Responder to automatically scan your email gateway tools across a variety of email attack vectors and respond to incidents by proactively removing threats from related email addresses. When you pair these solutions with Unify, you can quickly identify risky users, then alert, train, or otherwise mitigate them.
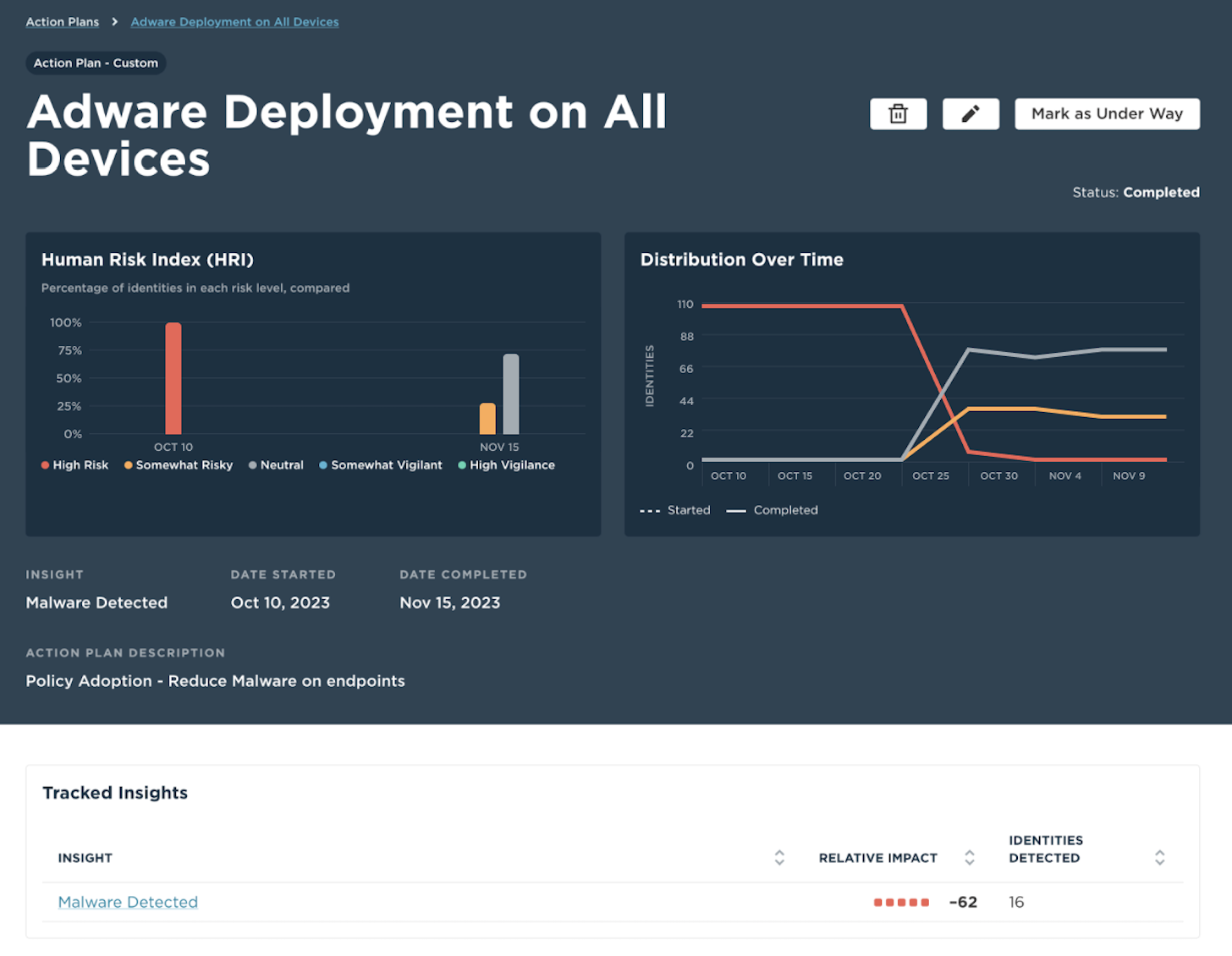
Policy Orchestration
Streamline workflows with a simple click. Turn tedious and repetitive policy playbook updates into the latest guidance to ensure teams know how to address emerging vulnerabilities.Create workflows that automatically update policy in other solutions within the security stack. For example, when a user’s risk increases, Unify can update the identity policy for that user within SailPoint IdentityIQ, thus automatically restricting access or enforcing a more strict access policy.
Nudge, Train, Phish, and Orchestrate with Unify HRM Action Plans.
 Identify
Identify
 Protect
Protect
 Report
Report

Feature
Human Risk Management Conference 2024
Join us for the 3rd Annual Human Risk Management Conference. Registration is now open.
Ready to see it in action?
Fortune 500 companies trust Living Security to deliver human risk management by using existing data to identify risky employees or teams and target immersive training to those who need it most. This approach keeps organizations ahead of breaches and enables them to track their progress toward a better security posture. This proactive, automated, efficient approach saves resources while keeping employees and data safe.
Schedule a meeting today and let's get started.


 Protect
Protect








