.jpg)
.jpg)
Solutions 
Solutions
Data Loss
Data leak incidents occur when data is destroyed, deleted, corrupted, shared or made unreadable outside of company policy or data privacy laws.
Data Loss is when data is somehow removed from your system completely and cannot be recovered or has left your controlled environment through unauthorized access and/or malicious intent.

The Living Security Unify HRM Platform gives you visibility into the most risky users for data leak and data loss based on behavior and context so you can take proactive steps to mitigate risk. Key insights include:
- Bulk Data Movement
- Sensitive Data Shared
- Suspicious Data Access
- Personal Data Leaked
- Data Transfer Blocked
 Identify
Identify
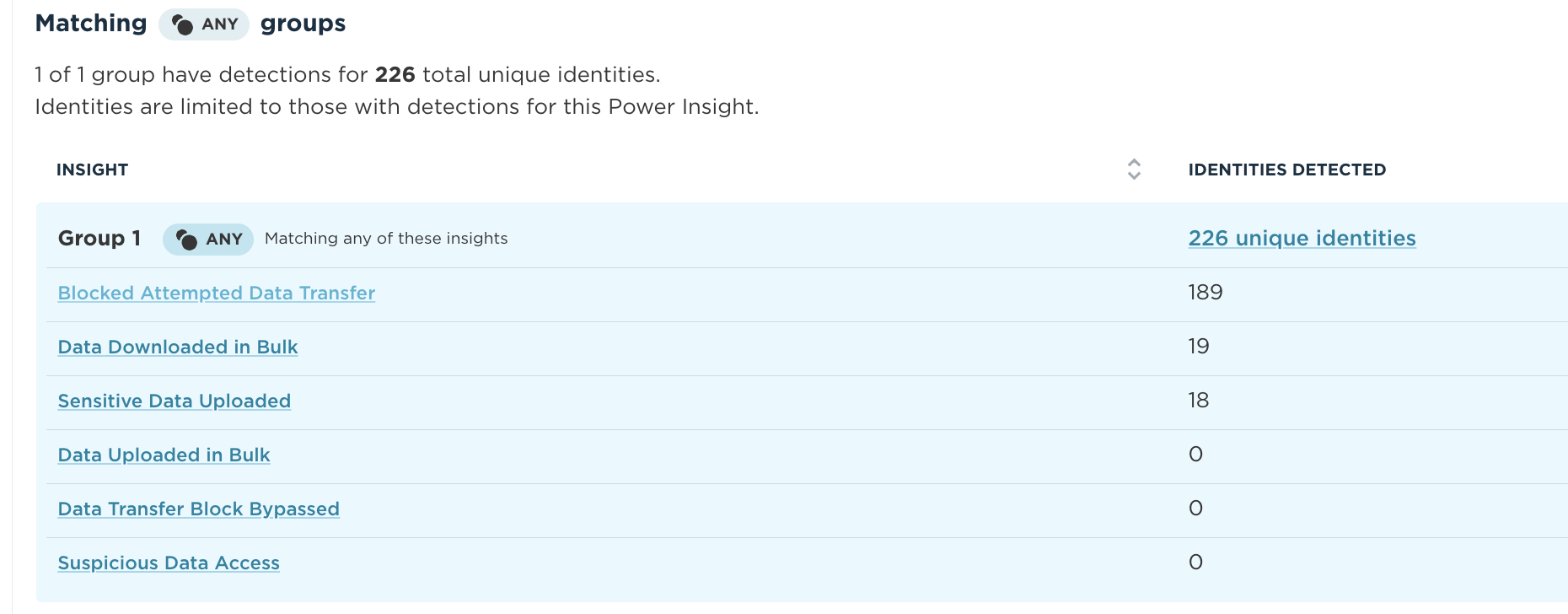
For the first time, visualize all events and behaviors from sensitive data access and sharing to data transfers and attempts in a single view. Drill into specific risky events, or track all potential risks under the Sharing Sensitive Data Power Insight.
In a single pane of glass, Unify helps you identify susceptibility to data loss by helping focus on the riskiest areas of the business, so that you can prevent data loss before it happens.
Dive Deeper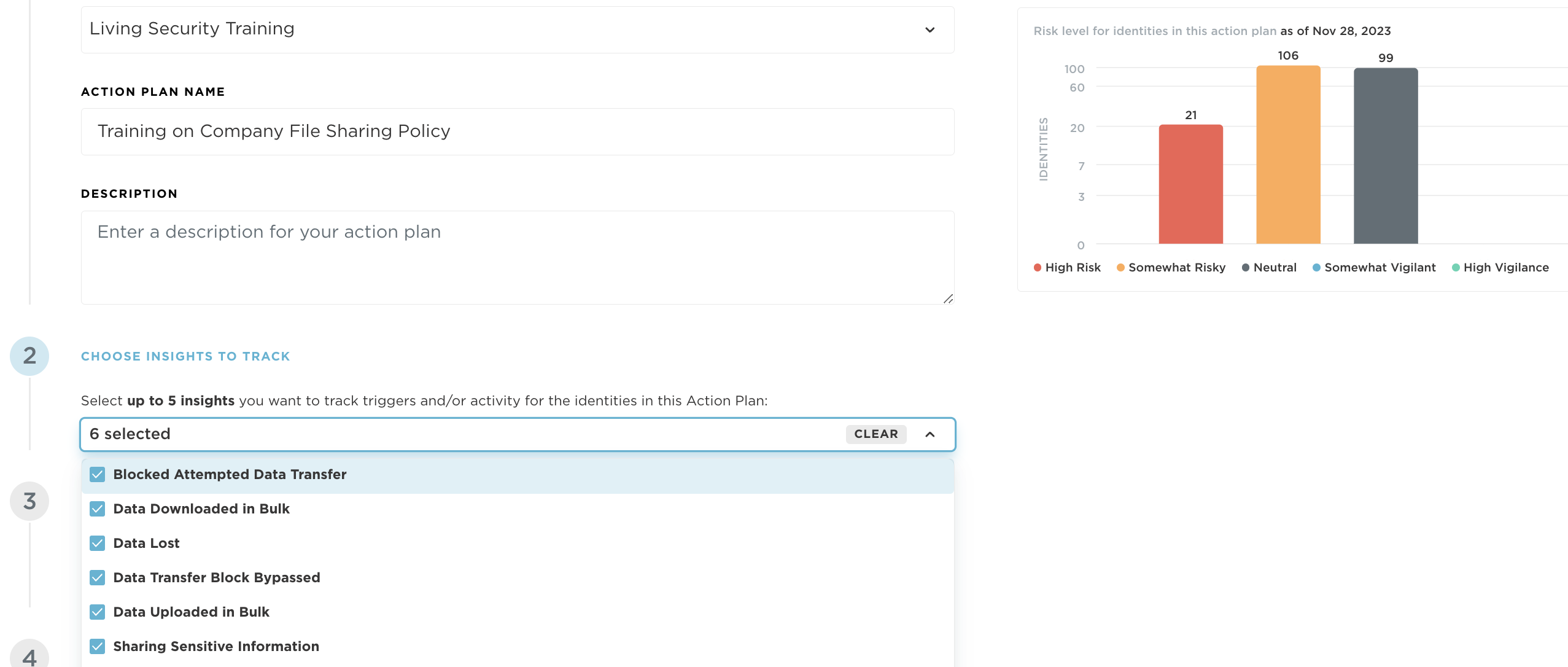
.png) Protect
Protect
Initiate action plans that include nudges, training, and policy interventions as soon as risky data leak or data movement activities are observed. Send notifications, deploy software or simply highlight the organizational policies around data sharing and observe the effect the interventions have on key risky areas in your organization.
Learn More
 Report
Report
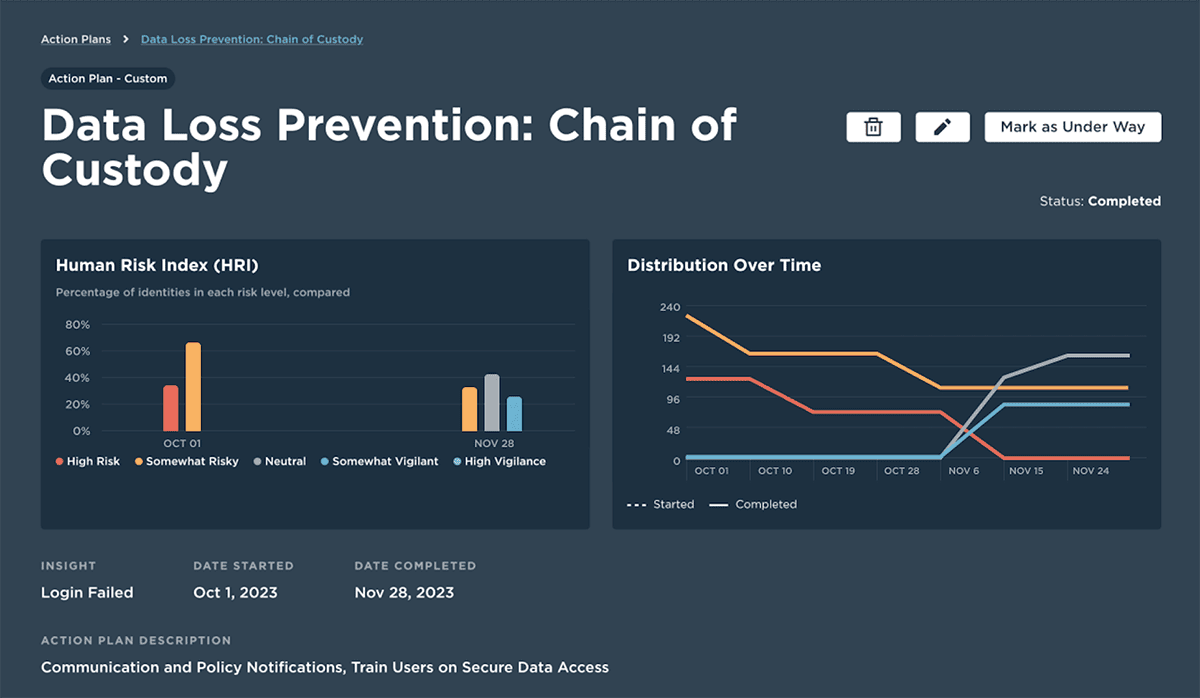
As soon as you take action to mitigate risk, use tailored reports that ensure the interventions are creating the desired effect. Beyond tracking training completion or policy acceptance, view the trends in the key behaviors. Ensure that risky data sharing and sensitive access events decrease, and demonstrate the ROI of the program.
Promote a positive culture of security vigilance. Use scorecards and reports for employees, managers, and executives to foster a security-conscious culture and boost employee vigilance.
Learn More





