.jpg)
.jpg)
Solutions 
Solutions
Phishing & Email
Phishing is a type of social engineering attack often used to steal user data. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.

The Living Security Unify HRM Platform gives you visibility into the most risky and vigilant users for phishing and email security based on behavior and context so you can take proactive steps to mitigate risk. Key insights include:
- Simulated Phish Clicked
- Real Phish Clicked
- Real Phish Targeted with Malware
- Phish Highly Targeted User
- Simulated Phish - Password Submitted
 Identify
Identify
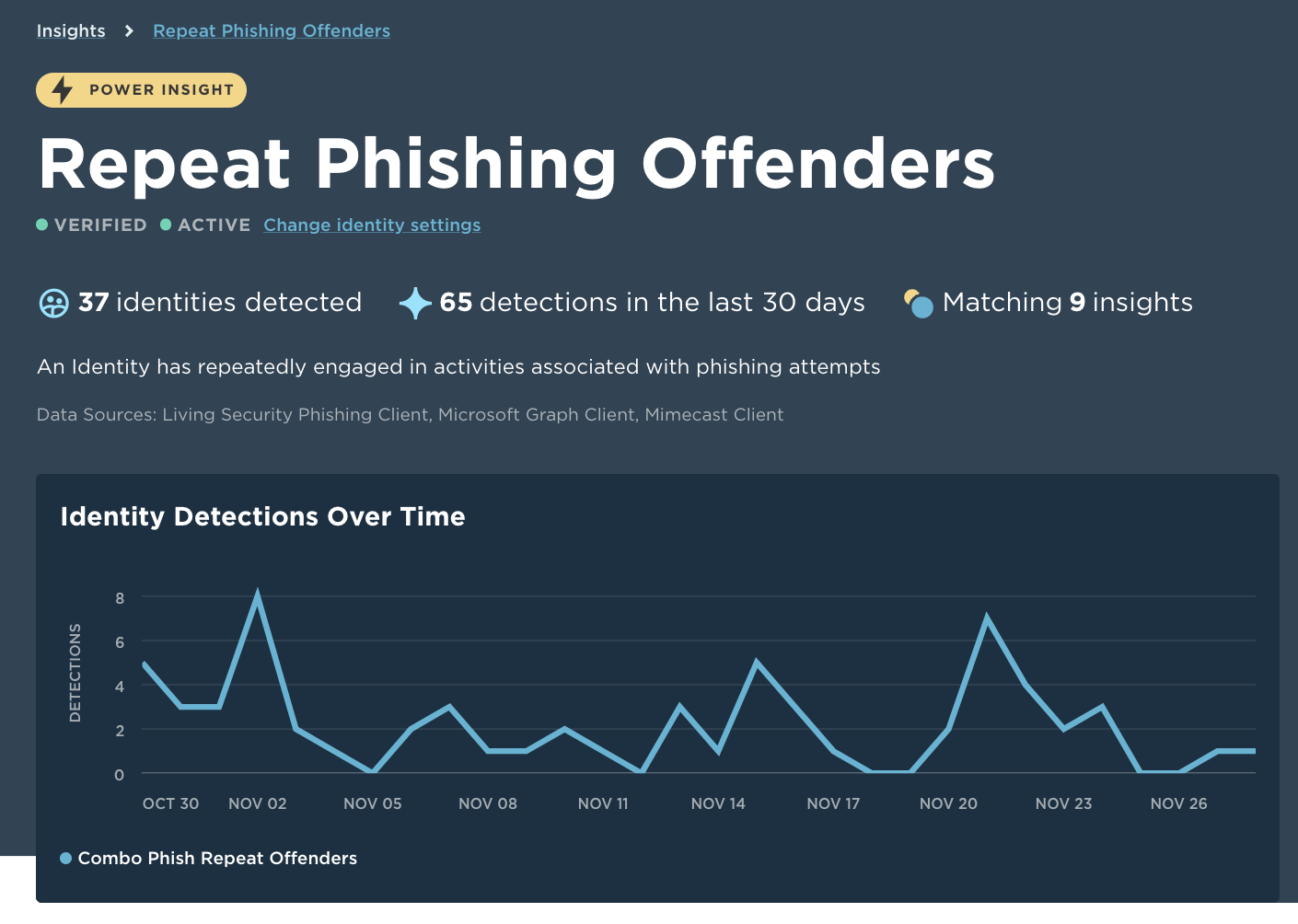
Visualize all phishing and email security data in a single view. Unify lets you correlate behaviors and threats across real phishing targets and incidents, and simulated phishing performance.
Rather than reporting on monthly company-wide click rates, focus on the end users that represent the highest social engineering risk to the organization. Which users have access to sensitive data and are repeatedly falling for phishing emails? Who is being targeted by real phish and failing simulations?
Dig Deeper
.png) Protect
Protect
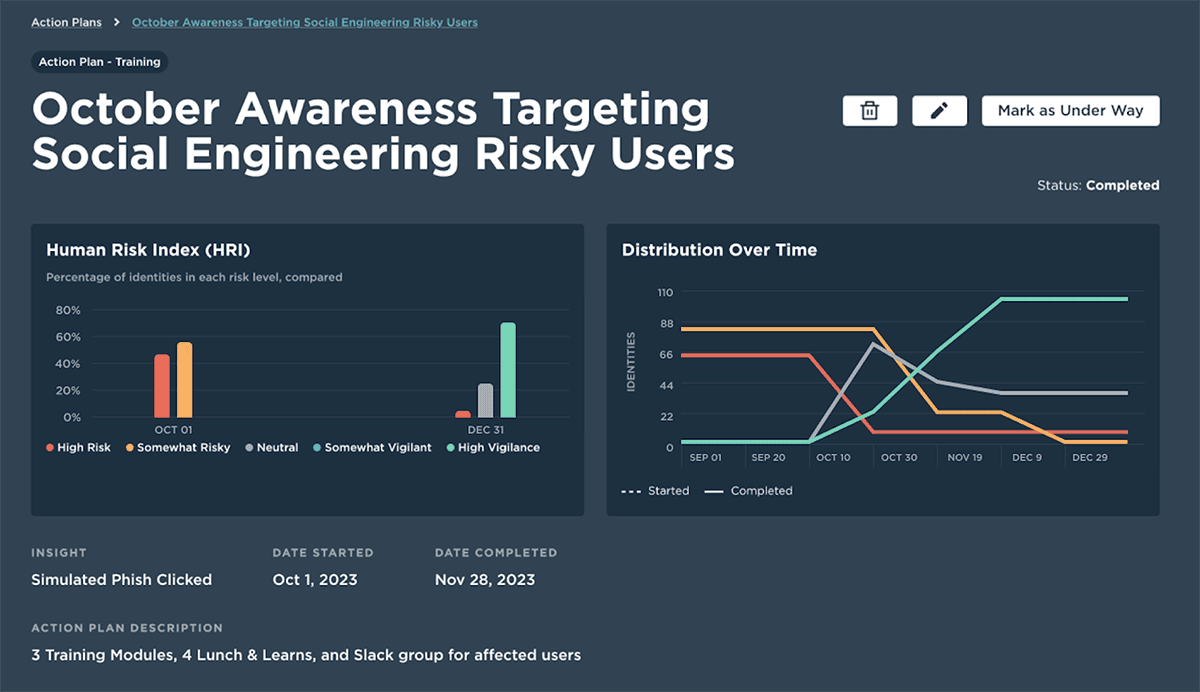
Stop the incident before it occurs. Initiate action plans that include nudges, training, and policy interventions based on key risky behaviors or levels of human risk. Send recommended content to risky users, or schedule a Lunch & Learn to highlight why specific roles need to be extra vigilant when it comes to social engineering threats.
Remove the tedious work of creating and sending generic training. Instead, spend your energy targeting key risks and tracking the ROI on the prescribed interventions.
Learn More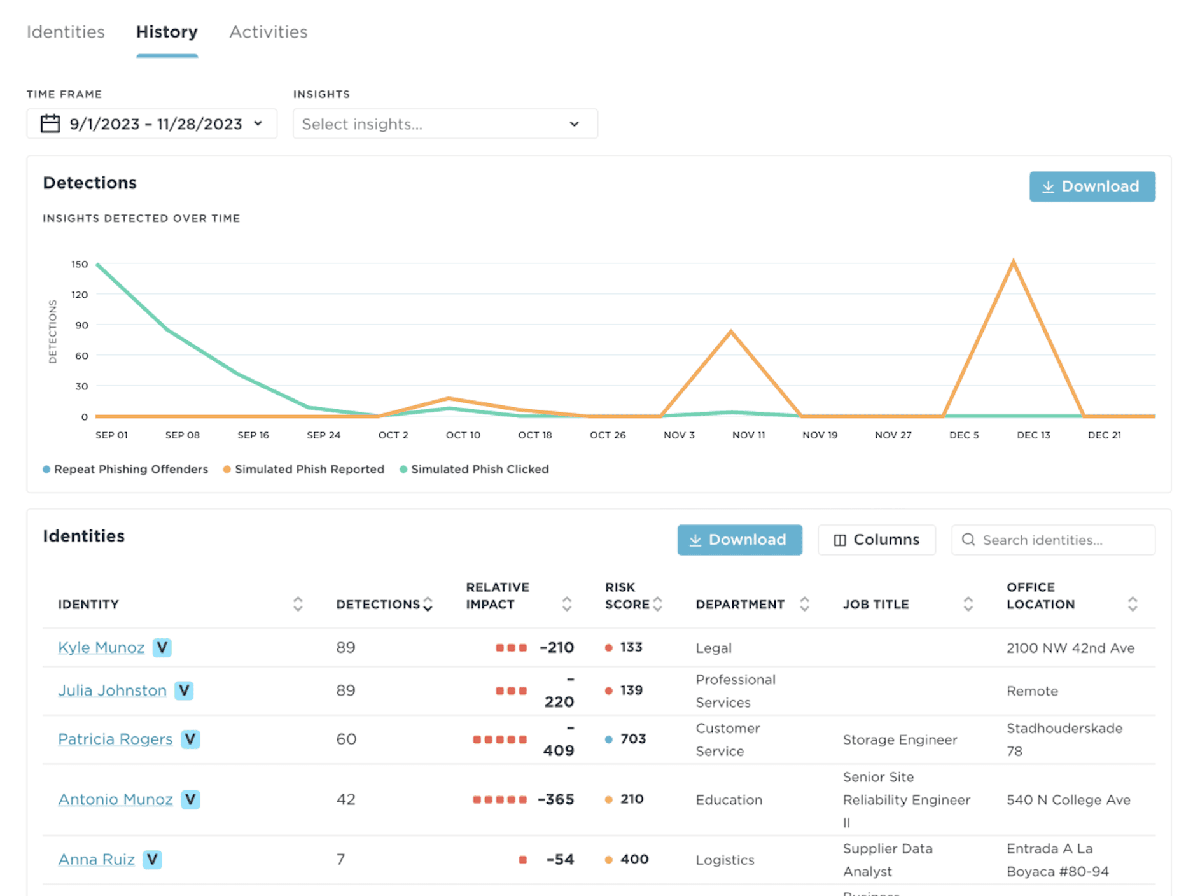
 Report
Report
Demonstrate ROI with tailored reports that ensure the interventions are creating the desired changes in behaviors. Beyond tracking training completion or policy acceptance, view the trends in the key behaviors. Watch email clicks reduce and email reporting and vigilance increase.
Turn your riskiest end users into vigilant assets and demonstrate their progress. Use scorecards and reports for employees, managers, and executives to foster a security-conscious culture and boost employee vigilance.
Learn More





