

Blogs 
May 16, 2025
Living Security Team
Guide: How to Transform Cybersecurity Awareness Month with AI-Powered, Risk-Based Training
Transform your Security Program From Awareness to Action in 4-Steps
Evolve Cybersecurity Awareness Month into a Risk-Reduction Movement
Why It’s Time to Transform
For 21 years, Cybersecurity Awareness Month has been a moment for IT and Security teams to rally their organizations. But the threats have changed. The stakes are higher. And expectations? They've evolved.
We can’t afford to settle for a month of games and posters. It’s time to lead with purpose, backed by data and driven by outcomes.
This isn’t just a guide. It’s a call to action for awareness teams to evolve from engagement-centric to risk-driven—where behavior change and measurable impact take center stage.
The Problem with “Awareness”
Yes, we’ve made cybersecurity more engaging. We’ve brought it into the spotlight. But after two decades of themed months and poster contests, it’s time to ask:
- What happens if we skip Cybersecurity Awareness Month this October?
- How does this align with our biggest risks?
- Can we prove impact beyond participation stats?
- Are we using our existing tools to support October’s goals?
- What’s the ROI—without vanity metrics?
If you can't confidently answer those questions, it's time to evolve.
The New Cybersecurity Awareness Month: From Tradition to Transformation
We’re not ditching the classics—webinars, games, fireside chats—they stay. But now, they’re aligned to outcomes, aimed at high-risk cohorts, and backed by data.
Follow these 4 steps to drive more strategic outcomes from Cybersecurity Awareness Month this year.
Step 1: Sharpen the Strategy
Slow down. Don’t start with calendars and themes. Start with intent. Ask your CISO:
“If we could only drive two meaningful behavior changes this Cybersecurity Awareness Month, what should they be—and why?”
From there, engage Incident Response. Find out what’s driving recurring incidents and use that insight to focus your campaign on the most problematic areas.
Step 2: Fuel the Campaign with Data
You already have the data. Now it’s time to use it to answer these critical questions:
- Email Security → Who’s being targeted most often?
- Phishing Simulators → Who’s clicking, reporting, or ignoring?
- IAM → Who has dangerous access or poor credential hygiene?
- Org Metadata → Which roles, departments, and regions show patterns of risky behavior?
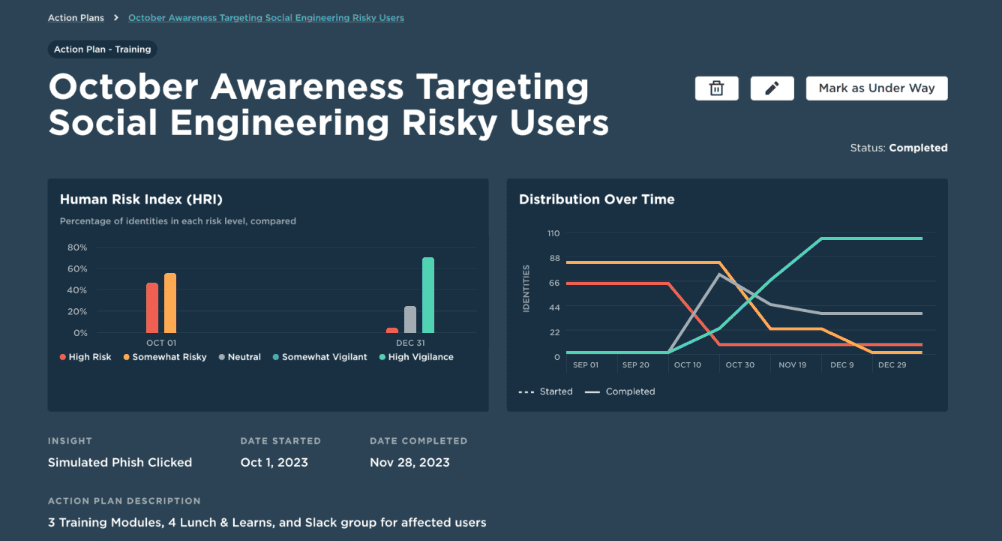
Living Security’s Unify platform applies AI-powered analytics to surface the answers to these questions. It identifies the riskiest behaviors in real-time—transforming fragmented data from phishing tools, IAM systems and email security into precise, actionable intelligence. This means you can move faster, target smarter and drive measurable outcomes without the manual effort or guesswork.

And with Living Security’s Human Intelligence Team (HInT), you don’t have to dig through the noise. It automatically identifies your riskiest users and gives you precise recommendations: who to target, what to deliver, and how to measure change.
Step 3: Baseline Behaviors and Segment Risk
Forget org-wide metrics. Zero in on what actually matters and set baselines so you can measure progress. Look at the data to determine:
- Who’s clicking and holds privileged access?
- Who’s a repeat clicker and hasn’t enabled MFA?
Then pinpoint risk-heavy departments:
- Which two business units show the most signs of social engineering or insider threat vulnerability?
With Unify and HInT, you can instantly slice and dice this data, identify behavior clusters, and deploy targeted, behavior-driven content experiences that resonate—and work.
Step 4: Gamify the Movement
You’re not running a campaign—you’re launching a cultural movement. And movements need momentum.
With Living Security’s complete toolkit, you’ll have everything ready:
- Leaderboards based on actual behavior improvement
- Prizes tied to security-positive actions: reporting phish, enabling MFA, rotating passwords
- Ready-to-launch content, promo emails, speakers, and live events
- Engagement assets already mapped to risk-informed goals
Unify makes it easy to track progress in real time—with dashboards that show vigilance rising and risk declining across teams. Let departments compete to be the most secure, and let the data declare the winner.

Some of Living Security’s customers saw significant results when identifying risky users and tracking before and after Cybersecurity Awareness Month efforts in October. Results include:
- A 40% drop in click rate among high-risk roles
- A 3x increase in phish reporting
- A measurable bump in password manager usage and MFA enablement
That’s not just awareness, that’s transformation.
This is not aspirational—it’s operational!
You already have:
- The tools
- The data
- The team
Now it's time to drive change.
Join the Movement
Living Security’s Unify equips you with:
- Customized dashboards
- Risk-aligned campaign content
- Strategic planning and peer support
Choose a path that will make the most impact for you and your organization.
| Phase | Toolkit Component | October Basics | October Rewired |
|---|---|---|---|
| Risk Identification | Human Risk Assessment Correlated human risk insights delivered through Living Security’s Unify—powered by your existing phishing and email data—to identify high-risk users. |
● | |
| Expert-Backed Insight Reports Living Security’s HInT experts supercharge your Unify report with human intelligence—delivering clear, expert-backed recommendations to eliminate your organization’s greatest risks. |
● | ||
| Planning | Risk-Based Engagement Content Attention-grabbing materials like puzzles and games, and quick-hit videos tailored to drive awareness exactly where your employees need it most. |
● | ● |
| Execution | Speakers Schedule a sought-after speaker with fascinating topics |
● | ● |
| Campaign in a Box Leverage weekly materials with blog posts, email messaging, chat communications, and more |
● | ● | |
| Promotional Assets & Campaign Guides Easy-to-use templates and campaign plans to boost employee participation and highlight your cybersecurity month success. |
● | ● | |
| CyberEscape Online Interactive risk challenges and simulations specifically crafted to test and reinforce key cybersecurity topics in an engaging storyline. |
● | ● | |
| Interactive Experience Participate in a family-friendly event that brings fun and learning to everyone. |
● | ● | |
| Reporting | Expert-Backed ROI Report Prove ROI, show impact, and make the case for future investment in human risk management—with no fluff, just results. |
● | |
| Expert-Backed Impact Report Actionable insights and success metrics delivered by Living Security’s HInT experts after your Cybersecurity Awareness Month activities, tracking behavior change, measuring risk reduction, and seeing what worked. |
● |
This October, don’t just raise awareness. Raise the bar. Contact a Living Security representative to get started.