Living Security Suite Whitelisting
This guide will serve to communicate the technical requirements of our products to your team. Getting an early start on these technical tasks and internal governance will ensure a seamless onboarding experience.
Table of Contents
System overview and security summary
URL Whitelisting
Whitelisting is an important component of integrating Living Security's suite of applications. Use the following guide to avoid connectivity issues:
Detailed whitelisting and troubleshooting by product:
| Description | Specific URL(s) | Port | Req'd? | Relevant Products |
| General |
*.livingsecurity.com |
443 | Yes | All |
| Contentful |
cdn.contenful.com images.ctfassets.net assets.ctfassets.net platform-cdn.livingsecurity.com |
443 | Yes | All |
| Unlayer |
api.unlayer.com api.events.unlayer.com |
443 | Yes | Training |
| Twilio | See article | Yes | CyberEscape Online |
|
| Firestore* | firestore.googleapis.com | 443 | Yes | |
| *.firebaseio.com | 443 | Yes | ||
| SendGrid (Dedicated IPs) |
198.37.157.57 |
N/A | Yes | All |
| LaunchDarkly |
events.launchdarkly.com app.launchdarkly.com |
443 | Yes | |
| Vitally |
*.vitally.io |
443 | Yes | |
| HubSpot |
api.hubspot.com forms.hubspot.com |
443 | No | |
|
cdn.acsbapp.com |
443 | No | ||
| Datadog |
rum-http-intake.logs.datadoghq.com |
443 | No | |
| Fonts |
fonts.googleapis.com fonts.gstatic.com oss.maxcdn.com |
443 | No | |
| User Pilot |
js.userpilot.io |
443 | No | CeO |
*For our international customers, we recommend you whitelist the below URLs so that your EU and APAC regions are not affected by whitelisting issues.
| Firebase EU | *.europe-west1.firebasedatabase.app | 443 |
| Firebase APAC | *.asia-southeast1.firebasedatabase.app | 433 |
- Living Security Teams Whitelisting
- Living Security Training Platform Whitelisting
- Living Security Phish Whitelisting
Phish Simulation Email Whitelisting
The Training Platform is able to send training invitations, notifications, and other emails directly to participants. To ensure these emails do not get flagged, blocked or filtered as a phishing or spam email, please whitelist our IP addresses:
| SMTP IP Address | SMTP PTR Record |
| 149.72.161.59 | o1.ptr4777.keepnetlabs.com |
| 149.72.42.201 | o2.ptr4175.keepnetlabs.com |
| 149.72.154.87 | o3.ptr8903.keepnetlabs.com |
| 37.1.145.36 | smtp1.keepnetlabs.com |
| 37.1.145.35 | smtp2.keepnetlabs.com |
Browser Compatibility and Desktop policies
The Living Security Training Platform is designed to work with most browsers but we currently only support the latest version of Microsoft Edge and Google Chrome. This is because the Platform utilizes libraries which may not support some older versions of browsers or specific features of certain browsers, including Internet Explorer (IE).
The Teams gameplay experience will utilize both the microphone and camera of each participant. If your organization restricts this for end users, please make an exception for our web applications.
For more information on setting these exceptions for your environment see Manage Chrome policies with Windows registry or Configuring Microsoft Edge policy settings on Windows.
Living Security Phish Reporter: Customization & Deployment
Phishing Reporter is an add-in that allows users to easily report a suspicious email to cyber security teams. This add-on is compatible with Outlook, Outlook Web Access, Outlook Desktop, Outlook Mobile, Office 365, and Google Workspace environments.
View configuration and deployment guide.
User Access
Currently, only Living Security Training supports Single Sign-On (SSO). We've made it really easy for you to set up SAML SSO from within your admin account.
Need help? Schedule a meeting!User Provisioning
Both Living Security Phish and Training support some type of automatic user provisioning. Training supports Just-in-Time (JIT), SCIM provisioning, and manual list uploads, whereas Phish supports strictly SCIM. Use the guides below to configure your provisioning method of choice:
- Living Security Training
- SCIM
- Just-in-Time (JiT)
- Manual Import
- Living Security Phish
Need to test or troubleshoot with a Living Security Technical Specialist? Schedule a meeting!
Security tool considerations
Security tools like ZScaler, Netskope, and Forcepoint have an optional setting that can make them act as an SSL Proxy. Some services (like Firebase) don’t like SSL Proxies sitting between them and users. If your organization uses one of these network security tools and are having trouble getting tests to pass, adding an SSL bypass rule will likely resolve blocking issues. You can find more detailed information on what this means and how to do this in the following articles:
- https://help.zscaler.com/zia/controlling-access-google-consumer-apps
- https://help.zscaler.com/zia/about-ssl-inspection
- https://help.zscaler.com/zia/configuring-ssl-inspection-policy
- https://docs.netskope.com/en/ssl-decryption.html
https://help.zscaler.com/zia/certificate-pinning-and-ssl-inspection
System overview and security summary
| Question | Response |
| What data does LS store for Teams? |
Name, password(when not using SSO), email, and public IP. The following is stored to improves user experience through NPS collection and feature tracking: browser, device type, OS, hostname, country, viewport width, viewport height, timezone, user roles, userID |
| What data does LS store for Training? | Name, password(when not using SSO), email, job title, job location, department, and public IP. |
| How does Living Security store data at rest? | Living Security data at rest is encrypted with AES 256 using AWS KMS standard keys for Training and Teams, custom keys per tenant for Unify. |
| How Does Living Security encrypt data in transit? | Living Security data in transit is encrypted with TLS 1.3 via Cloudflare. |
| Where does Living Security store data for training? | Living Security stores data in AWS-US-East1. Also there are subprocessors that store data in AWS-EU-West1 (Hotjar, App user monitoring). |
| Where does Living Security store data for Teams? | Living Security stores data in AWS-US-East1. Also there are subprocessors that store data in AWS-EU-West1 (Hotjar, App user monitoring), and Google US-central1 (firebase, used to synchronize the experience). |
| Who is the Platform as a Service provider? | AWS |
| Where is your AWS environment located? | AWS-US-East1 |
| Are you SOC Certified? | Living Security Teams is SOC 2 Type 1 certified for its products. |
| What is your backup policy? | Client session data is exported daily and sent to Snowflake for internal reporting and usage tracking. |
Architecture Diagrams
Living Security Unify Workflow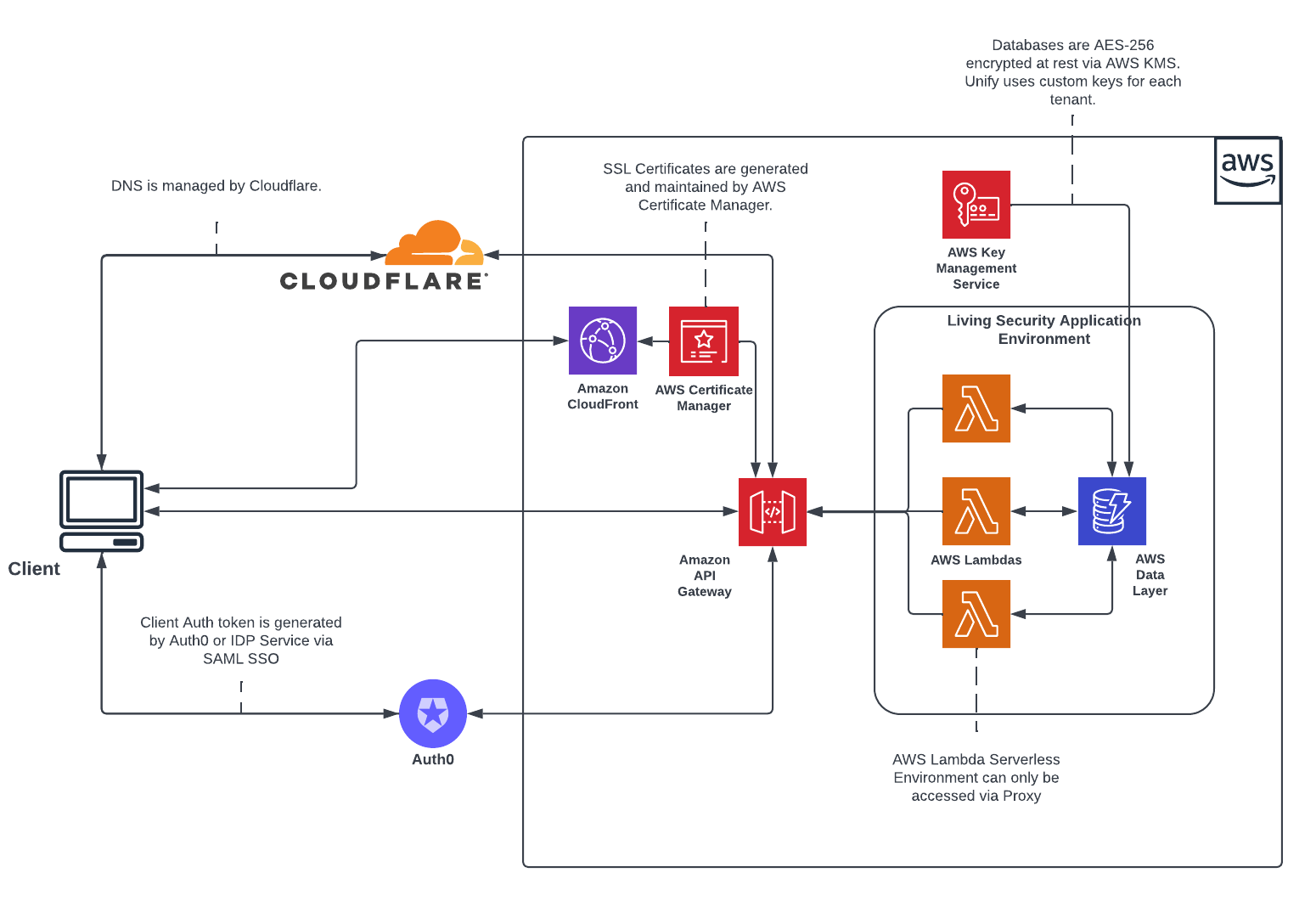
Living Security Teams Workflow

Living Security Training Workflow
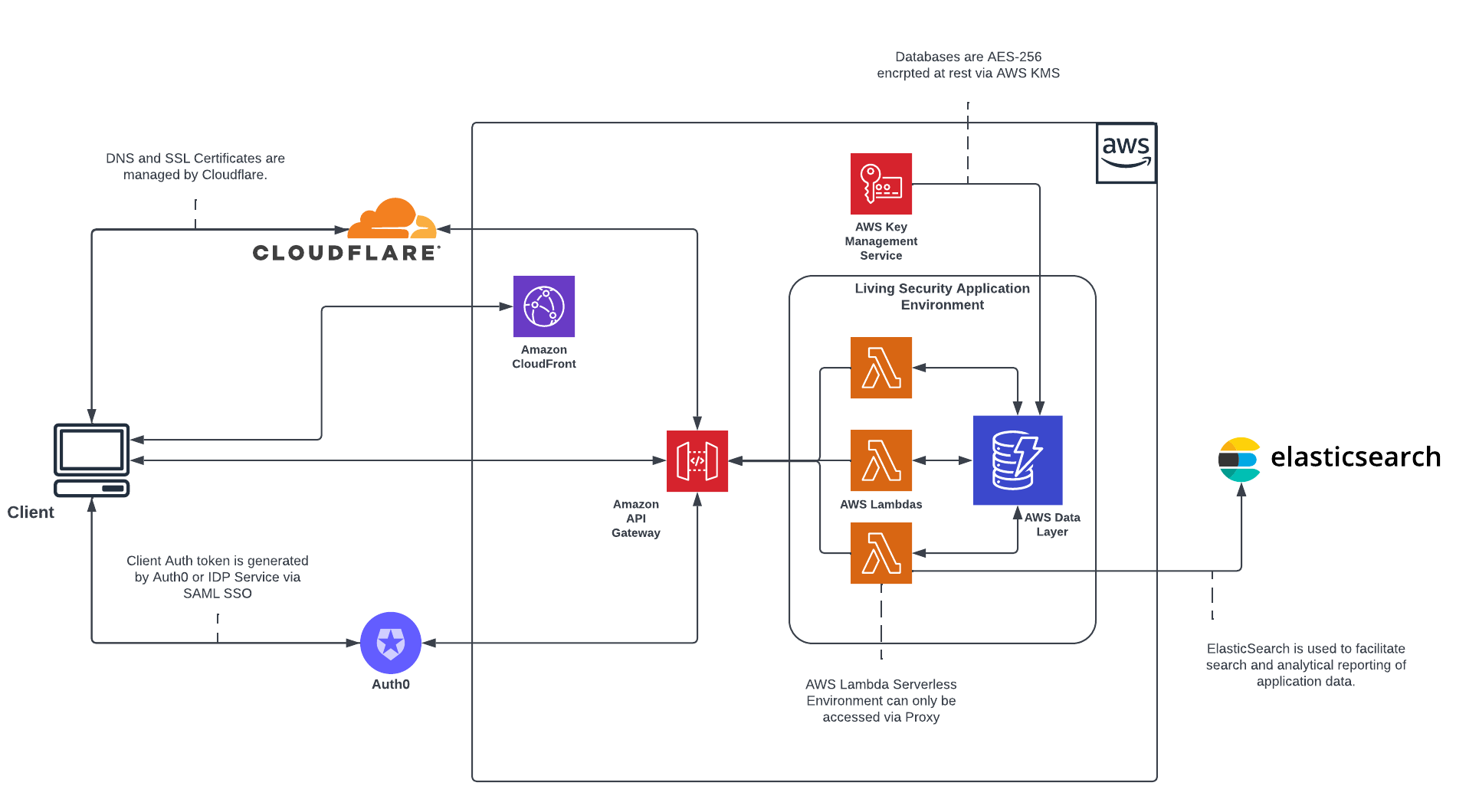
Note:
Before sending a security questionnaire please review our Shared Responsibility Model.
Need to test, troubleshoot, or schedule a working session? Click here!