What is PII?
Personally identifiable information (PII) 1 is any and all data that can be used to distinguish or trace an individual’s identity. PII is a core component of almost every compliance regulation whether for the government or the private sector.
While PII commonly includes - name, physical address, email address, date of birth, Social Security numbers, Government IDs, telephone number, biometric data and records, it has recently expanded to include more digital identifiers such as IP addresses, MAC addresses, geolocation data, login credentials and usernames, financial information and social media posts.

PII Is Categorized Into Two Groups of Data: Sensitive and Non-Sensitive.
The data type alone is not necessarily enough to categorize information as sensitive. A list of names and emails for your local bowling league is nowhere as potentially impactful as the names and emails for attendees at a defense contractor conference or patient contact information for a medical clinic.
Sensitive PII includes information that, when associated with an individual, could result in harm, embarrassment, inconvenience, or unfairness to an individual and impact them financially or socially. When transmitted electronically, it must be protected via encryption or other secure means.
No video selected
Select a video type in the sidebar.
Why It Is Important
All PII should be treated as sensitive, and you should err on the side of caution to protect PII for employees and customers.
Protecting PII requires secure transmission, secure storage (only stored on secured systems as well as only stored on devices that are encrypted), controlling the physical assets where that data is accessible (computers, phones must be locked or logged off if unattended), controlling the deletion and destruction and access to such information when in physical form.
Data Breaches are expensive, time-consuming, and can have long-lasting negative effects on an organization.

7 Steps on How To Secure PII

Common Challenges With Compliance-Based Training
When the aim is to complete training to satisfy compliance requirements, security awareness training becomes the goal - when in reality, better user recognition and user response to threats is what is needed.
Many organizations struggle to solve for the greatest challenge in cybersecurity - that we throw the best technology (the average enterprise has 75 different security products) at the problem, even though human error accounts for 90% of breaches. This is due to the fact that most trainings are boring, look only to check-the-box that compliance training has taken place, but do little to measure whether it actually made a difference in employee behavior.
What Does Good Look Like
Living Security is built on an entirely different premise - that people are your greatest asset. Our solution measures strengths and weaknesses for employees, identifies potential gaps, then delivers timely, engaging individual and team-based training that creates proven, lasting change. If your organization has ever struggled with challenges like: everyone has completed phishing training, but hundreds of employees still click on our phishing simulations over and over, you need a better solution.
The Escape Room is one example of a team training that explores phishing, PII, and other security concepts through team puzzle solving. Paired with an engaging storyline based on real life scenarios, the experience delivers a more impactful learning experience.
The goal of security awareness compliance shouldn’t just be to check the box that employees have completed training, it should be to prevent breaches and minimize risk and exposure due to human error.
A top five global telecommunications company ran an internal test and found that “end users who went through the LS Escape Rooms were 45% less likely to click on a phishing simulation vs. all others”.
What Makes Living Security Better
PII is at the center of most compliance regulations, and for good reason. When so many private details are collected and stored by so many vendors, the ability to safeguard and the need to protect our personally identifiable information from being exposed or compromised is critical to maintaining a level of security and privacy.
The most critical aspect of PII is the restriction of its collection and sharing. In order to protect your employees’, customers’ and clients’ PII, you need to train your employees. Living Security is chosen by more leading global organizations to provide the security awareness training they need to not only check the box for compliance, but to improve the cybersecurity posture of their organization. Training that is engaging, impactful, and delivers a 16x increase in retention helps you create proven, lasting change - and turns employees into your strongest cybersecurity asset.
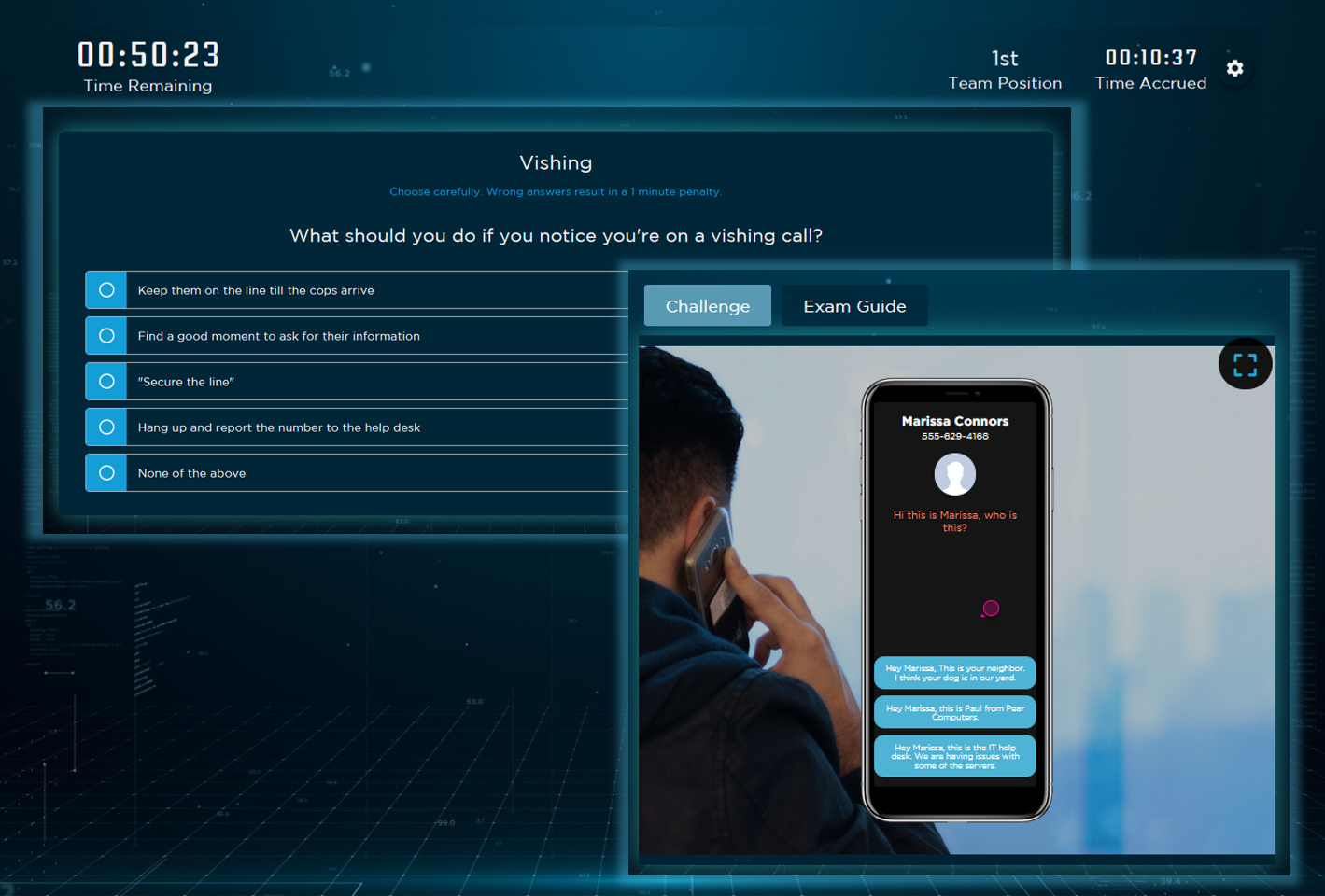
Living Security Makes It Easy To Meet Compliance With Training Modules, That Include, but Are Not Limited To:
- PII-specific content
- Passwords (maintaining strong passwords, use of a password manager)
- Phishing (and other forms, vishing, smishing)
- Physical security (device security, document access and disposal)
- How to report an incident
- Removable devices/USBs
- Mobile devices
- Privacy/PII
- Social media usage and risks of oversharing
- … many, many more
Our modules range from quick-hit 1-3 minute training per topic to full CyberEscape room series that cover multiple topics all-in-one. Your compliance checklist can easily support several complex topics in under 15 minutes.
Meet Your Compliance Requirements
Learn more about how Living Security can help you meet your compliance requirements, and actually help your employees make better cybersecurity decisions.
.svg)