How to Identify and Address False Positives on the Phishing Tool
If you are noticing unusual reporting results on your Phishing Campaigns, you may be running into false positives or false clicks. When reviewing your campaign results, we recommend checking the IP addresses for unusual opens or clicks on simulated emails. If there is a 100% click rate or you have identified IP addresses that don't belong to your organization, this can be due to false positives. This article will cover common reasons for false positives and tips on how to remedy this with your Team. Click on a section below to review:
- What is considered a click on the Phishing Tool?
- Identifying possible Bot Clicks through the Phishing Campaign Reports
- Understanding Bot Activity vs. Human Activity in Reports
- Common Causes for Unexpected IP addresses in Campaign Report Results
- How to Prevent False Positives
What is Considered a Click on the Phishing Tool?
A "click" is how our phishing tool is able to track risky user behavior by clicking a unique tokenized link on a phishing simulation email. However, there are other ways a click can be registered by our tool. Any click that is not conducted by the user is considered a false positive. Meaning, the user did not perform that action which can skew your reporting numbers. Here are some common reasons for false positives on phishing simulation emails:
- Improper whitelisting of your spam filter. Improper whitelisting can cause automated clicks or "bot clicks".
- Additional whitelisting of your security infrastructure, spam folders, and any software that could be performing link analysis or link probing.
- Simulated emails forwarded from one user to another user. Clicks could be generated as a result of the forwarded email being sandboxed and checked by the mail server or because the recipient of the forwarded email clicked on the link.
- Endpoint security or antivirus software.
- Mail filters with any security add-on packs that have not been properly whitelisted.
- Link preview capabilities as part of mobile device operating systems.
- Security software embedded into mobile device management (MDM) systems.
Identifying possible Bot Clicks through the Phishing Campaign Reports
"Bot clicks" often occur due to improper or insufficient whitelisting. They are caused by an automated process within your infrastructure whether it be by link probing, link analysis, email screening, etc. You are able to identify bot clicks through campaign report inspection. Here are a few key indicators of a bot click:
- Timing of Email
- If a phishing simulation email has a reported action of opened, clicked, and even submitted (depending on the template) that has happened within the same minute of one another
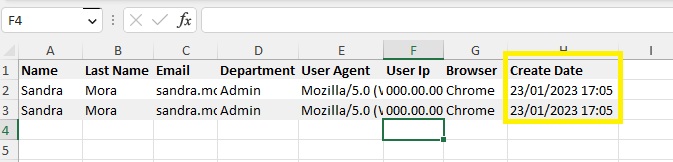
- If a phishing simulation email has a reported action of opened, clicked, and even submitted (depending on the template) that has happened within the same minute of one another
- A high number of Open/Clicks from one or multiple IP addresses
- We recommend analyzing the IP addresses and cross-referencing them with your security tools and adding the necessary whitelisting or IP exclusions from your security tools to minimize this from happening.
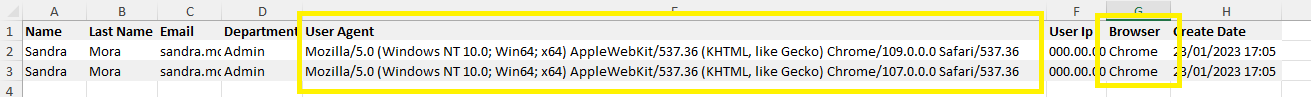
- The operating system is not an authorized OS in your environment.
- The Clicked tab of the report will show the browser and browser version. Ensure that the browser is not outdated and is not an excluded or restricted browser in your environment.
Understanding Bot Activity vs. Human Activity in Reports
In phishing campaign reports, Human Activity refers to real actions taken by users, such as opening emails, clicking links, or submitting data. In contrast, Bot Activity represents automated interactions triggered by email security systems, spam filters, or sandboxing tools. These bots scan emails and follow links as part of their protective duties, sometimes even before users see the message.
Bot activity may appear in both Opened Email and Clicked Link sections of the report. For example, if a security system opens an email to analyze it, or clicks a link to test the destination, these actions may be captured and flagged as bot interactions.
To ensure accurate reporting, the platform automatically detects and labels such activity based on predefined detection rules. Any record classified as Bot Activity will carry a special tag and can be excluded from the view by clicking the “Hide Bot Activity” button. Admins can also hover over the info (ⓘ) icon in the Activity Type column to see which rule was triggered.
The detection rules are:
-
A1 – Unusual User-Agent Interacted: Triggered when an atypical or suspicious user-agent (browser identifier) is detected.
-
A2 – Honeypot Link Reused: The hidden phishing link inside of the email clicked multiple times by the same IP and user-agent within 5 minutes—indicating automation.
-
A3 – Same-Second Activity Spike: Multiple activities occurred at the exact same time, which is unlikely for human users.
-
A4 – Stop Bot Activity Challenge Failed:
-
A4.1 – The phishing link was clicked, but the invisible browser javascript challenge was not passed.
-
A4.2 – The browser failed to load required scripts that a real user’s browser would normally execute.
-
If multiple entries are marked as Bot Activity, it usually means email security tools pre-screened the phishing simulation links. To focus on real user behavior, filter the report by Activity Type or use the “Hide Bot Activity” toggle. For more accurate results in future simulations, consider whitelisting our domains to minimize interference from automated systems.
By filtering out bot noise, organizations gain a clearer understanding of true user actions and risk levels.
Common Causes for Unexpected IP addresses in Campaign Report Results
When a click is registered in the console, the IP address is registered from where the “click” originated. Below are some examples of why you may see unexpected IP addresses:
- If a user is on a mobile device and clicks on the link, the click could show as coming from the cellular service provider.
- If a user is on the Wi-Fi in their house, the click would register as being from an IP address from that internet service provider (ISP).
- If a user is on public Wi-Fi, the click would register from the location of where the user was when they clicked.
- If you or one of your products uses a hosted services provider, such as AWS, the IP address may come from another location or even another country. Certain link analysis processes may not occur on the client side and the link may be “passed” to the security provider’s backend processing or analysis center.
How to try and Prevent False Positives
Being familiar with your infrastructure is the first step in preventing false positives. Since there are a wide variety of security software products, you may want to check the documentation of the software or service providers that you use to see if there is a section about exempting links or domains from link scanning, link analysis, or link probing.
We recommend launching test campaigns to test for any false positives in environments similar to your end-user's workstations/setup before launching a Campaign to a larger group. Download our Testing Template to guide you through prescriptive testing to ensure whitelisting is complete and to identify IP addresses to be excluded to avoid False Positives from occuring.
💡If false positives persist, we also recommend seeking help from your email security tool vendor on additional whitelisting needs.💡
Have additional questions? Feel free to contact us! We're happy to help.